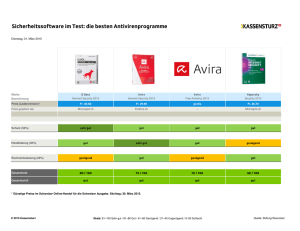
Werbung

CYBER SECURITY @ T-Sys t ems RSA Security Summit, München, 19. Mai 2015 Bernd König | Business Unit Cyber Security CYBER SECURITY @ T-Systems 2 Digit al is ier ung al l er Ges c häf t s ber eic he CYBER SECURITY @T-Systems 3 Cyber Threats Risiken Quelle: 2014 Data-Breach InvestigationsReport VerizonRisk Team US Secret Service DutchHigh-Tech Crime Unit Study April 2014 http://www.verizonenterprise.com/DBIR/2014/ CYBER SECURITY @T-Systems 4 Ok ös ys t emor ganis ier t er Cyber c r ime Reseller / Botnetz- Bullet-Proof-Hoster betreiber plant Straftat MalwareVerbreiter MalwareEntwickler Bot / Zombie Forenbetreiber C&C Frontend C&C Backend Datendiebe Drop Zone Legale Mitverdiener Anwerber von Quelle : Finanz- und Warenagenten Waren- bzw. Finanzagentenführer Finanzagenten Warenagenten CYBER SECURITY @T-Systems 5 Ges c häf t s model l OK CYBER SECURITY @T-Systems 6 Coming up s oon... Das IT-Sic her heit s ges et z 7 „Wir sind die Nummer Eins in Fragen der IT-Sicherheit für Großunternehmen; Mit der Cybersecurity-Partnerschaft bauen wir das Rüstzeug für die Abwehr von Cyber-Angriffen weiter aus.“ Reinhard Clemens, Telekom-Vorstand und CEO T-Systems. „Unsere Cybersecurity-Partnerschaft in Europa ermöglicht es Sicherheitsexperten, Werkzeuge für Analyse und Risikomanagement zu nutzen, um Unternehmensnetze gegen heutige ausgefeilte Cyberangriffe zu schützen.“ Art Coviello, former CEO RSA „Mit RSA haben wir einen verlässlichen und flexiblen Partner, der die speziellen Erfordernisse des deutschen Datenschutzes in seine Lösungen einfließen lässt.“ Dr. Jürgen Kohr, Senior Vice President Cyber Security, T-Systems CYBER SECURITY @T-Systems 8 Die alles durchdringende Transparenz Threat Actors IP: 192.173.1.21 Firewall Blocked Session IDS/IPS Blocked Session Malicious AntiVirus Username: JSMith FW Log Country: Brazil Risk: High Blocked Session Traffic DLP Alert Strong Authentication Alert Auth Log Asset: SQL Server Action: GET Network Session Agent: Firefox Session Data: HTTP/1.1 200 OK … Full Packet Capture ... Corporate Assets CYBER SECURITY @T-Systems 9 Wir haben jeder zeit ein ak t uel l es Lagebil d Sec ur it y s er vic es CYBER SECURITY @ T-Systems 10 PARADIGMENWECHSEL in Cyber s ec ur it y NOTWENDIG TRANSPARENZ KOMPETENZ Zunehmendes Wissen über Gefahrenlage Honeypots & Sicherheitstacho Simulationen Reduktion von Komplexität “Einfach sicher” CleanPipe Services Cyber Sec ur it y @ Deut s c he Tel ek om EINFACHHEIT Prävention, Erkennung und Reaktion Advanced Cyber Defense by Telekom Partnerschaft mit RSA Innovation durch Kooperation Partnerschaften mit komplementären Industrien Kooper at ion CYBER SECURITY @ T-Systems 11 Ent er pr is e - “ Sec ur it y is f or s har ing” Aust auschpl at t f or m f ür akt uel l e Mal war e THREAT FEEDs Ext er ne Quel l en Sit uat ional awar enes s PLATTFORM (s ammel n, VEREINSMITGLIEDER ver ar beit en, REPORTEN) Betrieb Auftrag Cyber Secur it y Ser vices wit h Incident Response Team Mal war e 1 CYBER SECURITY @T-Systems Mal war e 2 12 Was bedeut et ESARIS? 2 for large scale ICT production 6 workable (…we are using it) 1 Ordering and standardization schema Enterprise Security Architecture for Reliable ICT Services (ESARIS) 3 about security, assurance and trust 5 made for ICT service providers but works also for large IT departments 4 balancing between user organizations and provider CYBER SECURITY @T-Systems 13 ESARIS: Tr ans par enz f ür uns er e Kunden dur c h k l ar e Dir ek t iven f ür IT-Pr ovider Level 4: taxonomy and usage Corporate Security Rule Base L1 L2 Certification and 3rd Party Assurance Customer Communication and Security Service Management Corporate Security Policy Assurance to Customers Risk Management and Certification Evidence and Customer Relation Refinement Pyramid of Standards Vulnerability Assessment, Mitigation Plan Logging, Monitoring &Security Reporting Risk Management Release Mngt. and Acceptance Testing AB CDE Asset and Configuration Management System Development Life-Cycle Hardening, Provisioning &Maintenance Systems Acquisition and Contracting Security Patch Management Change and Problem Management Incident Handling and Forensics Business Continuity Management Customer and users ICT Security Principles L3 Data center Networks User Identity Management Provider Identity Management Mobile Workplace Security Office Workplace Security ICT Security Standards ICT Security Baselines L4 L5 Fulfillment Application and AM Security VM and S/W Image Mngt. Remote User Access Gateway and Central Services Computer Systems Security Database and Storage Security User LAN Periphery Corporate Provider Access Data Center Networks Operations Support Security Wide Area Network Security Data Center Security Administration Network Security Directives for Service and Production Attainment CYBER SECURITY @ T-Systems 14 War r oomin Bad Kr euznac h CYBER SECURITY @T-Systems 15 Advanc ed Cyber Def enc e BY TELEKOM Kompet enz f ür ent er pr is e Kunden TRANSPARENZ EINFACHHEIT KOMPETENZ kooper at ion Gebündel t e k ompet enzen Erstmalig Ende zu Ende Sicherheit durch Analyse von IT und Netzwerk Zielt auf die Entdeckung von gezielten Angriffen Schnellere Gegenmaßnahmen möglich Echtzeit Lagebild „Menschliche“ Experten für mehr Sicherheit Cons ul t ing & Int egr at ion Level 1 Analyst Level 2 Analyst Level 3 Analyst Analysis & Tools Support Analyst oper at ions Threat Intelligence Analyst SOC Manager CYBER SECURITY @T-Systems 16 Soc & CERT T-Sys t ems in Košice, Sl owakei CYBER SECURITY @T-Systems 17 next gener at ion s oc TRANSPARENZ EINFACHHEIT Sic her heit s s ys t eme Über bl ic k KOMPETENZ k ooper at ion Kont ext Firewall Business Anti Virus Risiko SIEM Data Loss Prevention Information Alerts Datenpakete Bedrohungen Rechner & Dateien Cont ent Int el l igenc e Workflow & Automatisierung, Regeln, Alarmierungsschwellen Thr eat Int el l igenc e Anal yt ic Int el l igenc e Level 1 Analyst Level 2 Analyst Level 3 Analyst Threat Analyst Expertise CYBER SECURITY @T-Systems 18 SoC T-Sys t ems Budapes t , Ungar n CYBER SECURITY @T-Systems 19 TELEKOM ADVANCED CYBER DEFENSE NG SECURITY OPERATIONS CENTER SERVICES Services & Processes (e.g., Help Desk, Ticketing, Network/ Platform/ System/ Application Operations) Asset Information NG SOC Operations Customer Enterprise IT Consulting & Integration Advanced Cyber Defense by Telekom Strategy Architecture Transformation Response Intelligence Customer CSIRT Situation Center Mgt. Escalation External Com. Crisis Mgt. Content Engineering Incident Detection & Response Cyber Situational Awareness Platform Operations Further security systems (Firewalls, IDS/IPS, Anti-Virus, SIEM, …) Network Recording Cyber Threat Information Feeds 360° Security by Deutsche Telekom & T-Systems 25.05.2015 20 Unif ied Sec ur it y Management Ser vic e . 360¨ Anal ys is . • Daten sammeln • Kritische Systeme und Daten identifizieren „Big Data Analyse“ • • • SIEM Event Correlation Incident Response Compliance Control (PCI, HIPAA, ISO) Analyse des Netzwerkverkehrs auf Anomalien • • • Central Log Server Data Collectors T • • • Active/Passive Network Scanning Asset Inventory Host-based Software Inventory Schwachstellen der eigenen IT identifizieren Log Collection NetflowAnalysis Service Availability Monitoring • • • Erkennen von Angriffen • • • Vulnerability Monitoring Active Scanning Network IDS Host IDS Wireless IDS File Integrity Monitoring Kooper at ion ent wickl ung VON secur it y ser vices MIT PARTNERN TRANSPARENZ EINFACHHEIT Idea Phas e Cr eat ivit y Concept ion Make decisions Impl ement at ion Speed KOMPETENZ kooper at ion Commer cial izat ion Cost s IPSfor Mobile Advanced Malware Protection Deep Packet Inspection APT Detection in the cloud Mobile Threat Detection Cloud Encryption Harddisk Encryption APT Detection and SoC Software SDN –Stealth Big Data Forensic Scout ing/ Cyber Secur it y Boot camp Scouting in Tel-Aviv, Silicon Valley, Europa Early/Late-Stage Startups Cyber Security Bootcamps im September in Berlin Ziel: Generierung und Identifizierung neuer disruptiver Ansätze für neue Produkte ACD by Tel ek om Kernelement des (Cyber) Security Portfolio Strategische Partnerschaft mit RSA und KPMG Modulares Konzept CYBER SECURITY @T-Systems 22 Ber nd König +49 (0) 171 110 4357 Head of Innovat ion Bus ines s Unit Cyber Sec ur it y CISSP, IT-Sachverständiger im Ring Deutscher Gutachter [email protected] T-Systems International GmbH Friedrich-Ebert-Allee 140 53113 Bonn CYBER SECURITY @T-Systems 23