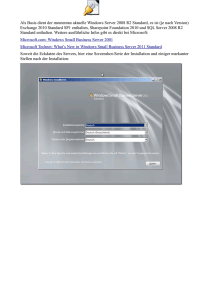
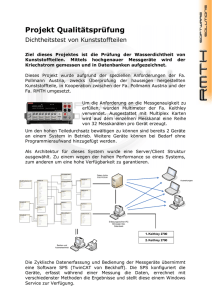
Microsoft Hyper-V und System Center
Werbung

Auf einen Blick Auf einen Blick 1 Einleitung ................................................................................................................. 19 2 Hyper-V im Überblick ........................................................................................... 55 3 Den Host-Server einrichten ................................................................................ 105 4 Host-Farmen und Verfügbarkeit ...................................................................... 277 5 Virtuelle Maschinen .............................................................................................. 389 6 System Center Virtual Machine Manager 2012 .......................................... 553 7 Daten wiederherstellen und Probleme beheben ....................................... 629 8 Migration und Aktualisierung ........................................................................... 721 9 Remotedesktopdienste ....................................................................................... 757 10 Finale und Ausblick ............................................................................................... 809 Inhalt Inhalt Geleitwort .............................................................................................................................................. 17 1 Einleitung 19 1.1 Was wir Ihnen bieten ........................................................................................................ 19 1.1.1 1.1.2 Das Buch als Ganzes ........................................................................................... Die zehn Kapitel ................................................................................................... 20 21 Die Autoren ........................................................................................................................... 28 1.2.1 1.2.2 1.2.3 1.2.4 1.2.5 Nicholas Dille ........................................................................................................ Marc Grote ............................................................................................................. Nils Kaczenski ....................................................................................................... Jan Kappen ............................................................................................................. Danke! ..................................................................................................................... 28 29 29 30 30 Warum virtualisieren wir eigentlich? ........................................................................ 32 1.3.1 1.3.2 1.3.3 Ein Projekt ohne Ziel kann nur scheitern ..................................................... Vor- und Nachteile abwägen ........................................................................... Stolperfallen vermeiden .................................................................................... 34 35 36 Virtuelle Welten: Die Fallstudien ................................................................................ 40 1.4.1 1.4.2 Die A. Datum GmbH ........................................................................................... Die Contoso AG .................................................................................................... 40 42 Hyper-V und der Virtualisierungsmarkt ................................................................... 44 1.5.1 1.5.2 1.5.3 46 47 50 1.2 1.3 1.4 1.5 Server-Virtualisierung: Eine Historie ............................................................. Die drei Großen am Markt ................................................................................ Microsofts Virtualisierungsweg ..................................................................... 2 Hyper-V im Überblick 55 2.1 Die Architektur ..................................................................................................................... 57 2.1.1 2.1.2 2.1.3 2.1.4 57 58 60 61 Hypervisor Typ 1 ................................................................................................... Hypervisor Typ 2 ................................................................................................... Monolithischer Hypervisor ............................................................................... Microkernel-Hypervisor ..................................................................................... 5 Inhalt 2.2 Paravirtualisierung und Emulation ............................................................................ 62 2.3 Hardware-Virtualisierung ............................................................................................... 63 2.4 Der VMBus und die Integration Services .................................................................. 64 2.5 Die Parent Partition ........................................................................................................... 67 2.6 Der Virtualisierungs-Stack .............................................................................................. 69 2.6.1 2.6.2 2.6.3 2.6.4 Virtual Machine Management Service ......................................................... Virtual Machine Worker Process .................................................................... Virtual Devices ...................................................................................................... Virtualization Service Providers und Virtualization Service Clients ... 69 70 71 72 Child Partitions .................................................................................................................... 72 2.7.1 2.7.2 An Hyper-V angepasste Gast-Systeme ......................................................... Nicht an Hyper-V angepasste Gast-Systeme ............................................. 73 73 2.8 Best Practices Analyzer .................................................................................................... 74 2.9 Vergleich mit Hyper-V 2.0 ............................................................................................... 76 2.9.1 2.9.2 Zahlen, Daten, Fakten ........................................................................................ Die großen und kleinen Erweiterungen ....................................................... 76 78 Virtuelle Gäste ..................................................................................................................... 79 2.10.1 2.10.2 2.10.3 Funktionierende und unterstützte VM-Betriebssysteme ...................... Technische Limits ................................................................................................ Alte Betriebssysteme betreiben ..................................................................... 79 81 83 Mit der PowerShell administrieren ............................................................................ 84 2.11.1 2.11.2 Der Einstieg ............................................................................................................ Beispiel-Skripte ..................................................................................................... 84 89 Microsoft Hyper-V Server 2012 ..................................................................................... 92 2.12.1 2.12.2 2.12.3 2.12.4 Installieren und einrichten ............................................................................... Auf einem USB-Stick installieren ................................................................... Hyper-V Server 2012 ohne Domäne verwalten .......................................... Dritthersteller-Tools zur Verwaltung nutzen ............................................ 92 95 97 99 Hyper-V auf dem Client ................................................................................................... 100 2.13.1 2.13.2 2.13.3 Anforderungen und Einschränkungen ......................................................... Installieren und Nutzen ..................................................................................... Windows Server 2012 remote verwalten ..................................................... 101 101 103 Zusammenfassung ............................................................................................................. 104 2.7 2.10 2.11 2.12 2.13 2.14 6 Inhalt 3 Den Host-Server einrichten 105 3.1 Die Grundinstallation ....................................................................................................... 105 3.1.1 3.1.2 3.1.3 3.1.4 3.1.5 3.1.6 Festplatten richtig aufteilen ............................................................................ Die CPU auswählen ............................................................................................. GUI vs. Server Core .............................................................................................. Die Speicherpfade ............................................................................................... Die Host-Reserven ............................................................................................... Die Auslagerungsdatei im Management OS .............................................. 106 106 107 112 113 115 Der Arbeitsspeicher ............................................................................................................ 116 3.2.1 3.2.2 3.2.3 3.2.4 3.2.5 3.2.6 3.2.7 3.2.8 3.2.9 3.2.10 Arbeitsspeicher »überbuchen«? ..................................................................... Hyper-V und der statische Arbeitsspeicher ................................................ Dynamic Memory – ein Ausweg? ................................................................... Wie Dynamic Memory funktioniert .............................................................. Dynamic Memory konfigurieren .................................................................... Smart Paging ......................................................................................................... NUMA-Einstellungen ......................................................................................... Arbeitsspeicher und das Storage-System .................................................... Einschränkungen von Dynamic Memory .................................................... Empfehlungen zu Dynamic Memory ............................................................ 118 119 120 123 125 126 127 128 129 132 Das Netzwerk ....................................................................................................................... 133 3.3.1 3.3.2 3.3.3 3.3.4 3.3.5 3.3.6 3.3.7 3.3.8 3.3.9 3.3.10 3.3.11 3.3.12 Wie das Netzwerk in Hyper-V funktioniert ................................................. Virtuelle Switches einrichten .......................................................................... Netzwerktypen in Hyper-V ............................................................................... Hyper-V-Netzwerke konfigurieren ................................................................ Sprechende Namen wählen ............................................................................. Hardware-Spezialitäten .................................................................................... Netzwerkkarten-Teams einrichten ................................................................ Erweiterbare Netzwerk-Switches .................................................................. 10-Gigabit-Netzwerke ........................................................................................ Hyper-V-Netzwerkvirtualisierung .................................................................. Empfehlungen zu Netzwerken in Hyper-V ................................................. Fallbeispiele für das Netzwerk ........................................................................ 134 143 149 154 160 163 171 178 187 196 205 207 Der Datenspeicher .............................................................................................................. 209 3.4.1 3.4.2 3.4.3 3.4.4 3.4.5 210 219 222 228 237 3.2 3.3 3.4 Crashkurs Storage: DAS, NAS, SAN oder was? ........................................... Welches Speichersystem brauche ich wann? ............................................ Lokalen Speicher konfigurieren ...................................................................... Storage Spaces verwenden .............................................................................. iSCSI-Target mit Windows Server 2012 ........................................................ 7 Inhalt 3.4.6 3.4.7 3.4.8 SAN-Speicher anbinden ..................................................................................... vSAN einrichten .................................................................................................... Fallbeispiele für den Datenspeicher .............................................................. 243 246 250 Sicherheit beginnt beim Design ................................................................................... 252 3.5.1 3.5.2 3.5.3 3.5.4 3.5.5 3.5.6 3.5.7 3.5.8 3.5.9 VM-Umgebungen multiplizieren Nachlässigkeiten ................................ Ganzheitliche Sicherheitskonzepte ............................................................... Den Host absichern ............................................................................................. Firewall-Virtualisierung ..................................................................................... Port ACL ................................................................................................................... Hyper-V-Switch-Erweiterungen ..................................................................... CSV und Bitlocker ................................................................................................ Berechtigungen für Hyper-V verwalten ....................................................... Sollen die Hyper-V-Hosts in die Domäne? .................................................. 254 259 265 267 268 269 269 270 272 3.6 Zusammenfassung ............................................................................................................. 276 4 Host-Farmen und Verfügbarkeit 277 4.1 Warum ist Verfügbarkeit ein Thema? ....................................................................... 277 4.1.1 4.1.2 4.1.3 4.1.4 4.1.5 4.1.6 Was ist überhaupt Verfügbarkeit? ................................................................ Wie abhängig sind wir wirklich? .................................................................... Was ist eigentlich ein Ausfall? ........................................................................ Wenn Redundanz zum Problem wird ........................................................... Grenzen des Clusterings ................................................................................... Das Konzept entscheidet .................................................................................. 278 280 281 283 286 287 Failover-Clustering ............................................................................................................. 288 4.2.1 4.2.2 4.2.3 4.2.4 4.2.5 4.2.6 4.2.7 4.2.8 4.2.9 4.2.10 4.2.11 4.2.12 289 289 291 292 293 300 301 304 307 310 312 318 3.5 4.2 8 Überblick ................................................................................................................ Terminologie ......................................................................................................... Cluster-Arten ......................................................................................................... Historie des Windows-Clusterings ................................................................ Neuerungen im Failover-Cluster .................................................................... Hardware für einen Cluster .............................................................................. Cluster-Validierung ............................................................................................. Best Practices für Cluster .................................................................................. Cluster-Quorum ................................................................................................... Cluster-Speicher ................................................................................................... Einen Cluster einrichten .................................................................................... Cluster-Rollen ....................................................................................................... Inhalt 4.2.13 4.2.14 4.2.15 4.2.16 4.2.17 4.2.18 4.2.19 Failover-Cluster verwalten ............................................................................... Clusterfähiges Aktualisieren ............................................................................ Die Aufgabenplanung einbinden ................................................................... Node Vote Weights ............................................................................................. Node Drain ............................................................................................................. Virtual Machine Monitoring ............................................................................ Cluster per PowerShell verwalten .................................................................. 324 330 334 335 336 337 339 Speicher-Cluster mit Windows Server 2012 ............................................................ 340 4.3.1 4.3.2 Storage Spaces im Cluster ................................................................................ iSCSI-Target als Cluster-Rolle .......................................................................... 341 343 NAS statt SAN ....................................................................................................................... 344 4.4.1 4.4.2 Authentifizierung mit »CredSSP« .................................................................. Authentifizierung mit Kerberos ...................................................................... 344 345 4.5 Host-Cluster mit Hyper-V ................................................................................................ 347 4.6 Live-Migration ...................................................................................................................... 352 4.6.1 4.6.2 4.6.3 4.6.4 4.6.5 4.6.6 4.6.7 4.6.8 Funktionsweise .................................................................................................... Einsatzszenarien .................................................................................................. Voraussetzungen ................................................................................................. Konfiguration ........................................................................................................ Verwendung .......................................................................................................... Speicher-Live-Migration .................................................................................... Bandbreiten-Management .............................................................................. Live-Migration im Failover-Cluster ................................................................ 353 353 354 356 358 361 364 365 VM-Replikation .................................................................................................................... 366 4.7.1 4.7.2 4.7.3 4.7.4 4.7.5 4.7.6 4.7.7 4.7.8 4.7.9 Funktionsweise .................................................................................................... Die Hosts konfigurieren .................................................................................... VM-Replikation aktivieren ................................................................................ VMs konfigurieren ............................................................................................... Das Replikat ........................................................................................................... Replizierte VMs testen ....................................................................................... Geplantes Failover ............................................................................................... Das Replikat in Betrieb nehmen ..................................................................... Wiederherstellungspunkte .............................................................................. 367 368 369 375 379 381 383 384 387 Zusammenfassung ............................................................................................................. 388 4.3 4.4 4.7 4.8 9 Inhalt 5 Virtuelle Maschinen 389 5.1 Design und Sizing ............................................................................................................... 390 5.2 Ressourcen einer VM ......................................................................................................... 391 5.2.1 5.2.2 5.2.3 5.2.4 5.2.5 5.2.6 5.2.7 5.2.8 5.2.9 392 393 396 402 405 413 423 430 440 5.3 5.4 5.5 Ressourcen-Pools und Verbrauchsmessung ........................................................... 447 5.3.1 5.3.2 5.3.3 449 450 452 10 Verbrauchsmessung für einzelne VMs ........................................................ Ressourcen-Pools als Abrechnungsbasis ..................................................... Ressourcen-Pools einrichten ............................................................................ VM-Verwaltung mit VMConnect ................................................................................. 459 5.4.1 5.4.2 5.4.3 459 463 468 VMConnect nutzen ............................................................................................. Datenaustausch mit einer VM ........................................................................ Einstellungen innerhalb einer VM ................................................................. Arbeiten mit Vorlagen ...................................................................................................... 472 5.5.1 5.5.2 Sysprep .................................................................................................................... Vorlagen in System Center 2012 Virtual Machine Manager mit SP1 ..................................................................................................................... Sicherer Umgang mit SCVMM-Vorlagen ..................................................... Sicherer Umgang mit VM-Vorlagen .............................................................. 472 VM-Snapshots ...................................................................................................................... 477 5.6.1 5.6.2 5.6.3 5.6.4 5.6.5 5.6.6 5.6.7 477 478 480 481 482 485 487 5.5.3 5.5.4 5.6 Hyper-V und die USB-Schnittstelle ................................................................ VM erzeugen mit dem Assistenten ............................................................... VM-Eigenschaften bearbeiten ........................................................................ Arbeitsspeicher ..................................................................................................... Prozessor ................................................................................................................ Festplatten ............................................................................................................. LUNs in einer VM ................................................................................................. Netzwerkkarten ................................................................................................... Integrationsdienste ............................................................................................ Was ist ein Snapshot? ........................................................................................ Die Technik hinter einem Snapshot .............................................................. Die Erstellung eines Snapshots ....................................................................... Die Eigenschaften eines Snapshots .............................................................. Die Anwendung eines Snapshots .................................................................. Entfernen eines Snapshots ............................................................................... Der Export eines Snapshots ............................................................................. 474 475 477 Inhalt 5.7 Export und Import .............................................................................................................. 488 5.7.1 5.7.2 5.7.3 Der Export .............................................................................................................. Export von Snapshots ........................................................................................ Der Import .............................................................................................................. 488 489 490 Offline-VMs verwalten ..................................................................................................... 494 5.8.1 5.8.2 5.8.3 5.8.4 5.8.5 5.8.6 Windows ohne Setup installieren .................................................................. Rollen in VHDs installieren ............................................................................... Windows Updates in VHDs installieren ....................................................... Virtual Machine Servicing Tool ....................................................................... Unbeaufsichtigte Konfiguration einer VHD ............................................... VHDs optimieren ................................................................................................. 494 496 499 501 508 509 Linux-VMs installieren ..................................................................................................... 510 5.9.1 5.9.2 5.9.3 5.9.4 Die Integration Services für Linux .................................................................. Die Installation einer Linux-VM ...................................................................... Die Kompilierung eines eigenen Kernels ..................................................... Erfahrungen mit dem Betrieb ......................................................................... 510 511 516 518 Server-Applikationen in VMs betreiben ................................................................... 520 5.10.1 5.10.2 5.10.3 5.10.4 Microsofts Support-Policy ................................................................................ Gast-Cluster ........................................................................................................... Active Directory .................................................................................................... Exchange Server ................................................................................................... 521 522 523 532 5.10.5 5.10.6 5.10.7 SQL Server ............................................................................................................... Oracle Database ................................................................................................... SharePoint .............................................................................................................. 543 548 550 5.11 Zusammenfassung ............................................................................................................. 552 6 System Center Virtual Machine Manager 2012 553 6.1 Funktionen des SCVMMs 2012 ...................................................................................... 553 6.1.1 6.1.2 6.1.3 6.1.4 6.1.5 6.1.6 6.1.7 6.1.8 554 554 554 554 555 555 555 555 5.8 5.9 5.10 P2V-Funktionen .................................................................................................... V2V-Funktionen ................................................................................................... Zentrale Verwaltungskonsole ......................................................................... Zentrale Bibliothek .............................................................................................. Bare Metal Provisioning .................................................................................... Update- und Compliance-Management ..................................................... Storage-Management ........................................................................................ Ressourcenoptimierung .................................................................................... 11 Inhalt 6.2 Neuerungen in SCVMM 2012 ......................................................................................... 6.3 SCVMM 2012 installieren ................................................................................................. 556 6.3.1 6.3.2 6.3.3 Datenbank ............................................................................................................. Installationsvoraussetzungen ......................................................................... Installationsprozess ............................................................................................ 557 557 559 SCVMM 2012 konfigurieren ............................................................................................ 566 6.4.1 6.4.2 6.4.3 6.4.4 6.4.5 6.4.6 6.4.7 6.4.8 6.4.9 6.4.10 6.4.11 6.4.12 6.4.13 Host-Gruppen erzeugen .................................................................................... Ausführungskonten erstellen .......................................................................... Fabric-Management konfigurieren ............................................................... Einstellungen ........................................................................................................ Aufträge .................................................................................................................. Bibliothek ............................................................................................................... SCVMM-Vorlagen verwalten ........................................................................... Profile in SCVMM erstellen ............................................................................... Physische Maschinen in virtuelle Maschinen umwandeln ................... Virtuelle Maschinen zu virtuellen Maschinen migrieren ....................... Virtuelle Maschinen erzeugen ........................................................................ Eine private Cloud einrichten .......................................................................... Cloud zuweisen .................................................................................................... 566 569 570 578 581 582 583 583 590 593 594 596 600 System Center App Controller 2012 ............................................................................ 601 6.5.1 6.5.2 6.5.3 Neuerungen in App Controller Service Pack 1 ............................................ App Controller installieren ............................................................................... App Controller einsetzen .................................................................................. 602 602 606 Dynamische Optimierung und Energieoptimierung in SCVMM ................... 609 6.6.1 6.6.2 Dynamische Optimierung ................................................................................ Energieoptimierung ............................................................................................ 610 612 Update-Management ....................................................................................................... 614 6.7.1 6.7.2 WSUS-Server zu SCVMM hinzufügen ........................................................... Update-Basislinie konfigurieren ..................................................................... 615 617 SCVMM-Datensicherung und Wiederherstellung ............................................... 619 6.8.1 6.8.2 SCVMM-Datenbankwiederherstellung ........................................................ Weitere SCVMM-Konfigurationselemente sichern ................................. 620 620 VMware vSphere und Citrix XenServer integrieren ............................................ 621 6.9.1 6.9.2 6.9.3 6.9.4 621 621 622 623 6.4 6.5 6.6 6.7 6.8 6.9 12 Unterstützung von VMware vSphere und ESX-Hosts ............................. Unterschiede zu SCVMM 2008 R2 ................................................................. Systemvoraussetzungen ................................................................................... VMware vCenter Server zu SCVMM hinzufügen ...................................... 555 Inhalt 6.9.5 6.9.6 6.9.7 6.9.8 Vorlagen eines VMware vCenter Servers hinzufügen ............................. Citrix XenServer .................................................................................................... Systemvoraussetzungen ................................................................................... Einschränkungen der Verwaltung von VMware vCenter ...................... 624 624 625 626 Migration von SCVMM 2008 R2 zu SCVMM 2012 ................................................. 626 6.10.1 6.10.2 Update von SCVMM 2008 R2 zu SCVMM 2012 ohne SP1 ....................... Upgrade von SCVMM 2008 R2 zu SCVMM 2012 mit SP1 ........................ 627 627 6.11 Zusammenfassung ............................................................................................................. 628 7 Daten wiederherstellen und Probleme beheben 629 7.1 Restore ist mehr als Backup! ......................................................................................... 629 7.2 Anforderungen klären ...................................................................................................... 631 7.3 Methoden auswählen ....................................................................................................... 634 7.4 Ebenen des Backups .......................................................................................................... 634 7.4.1 7.4.2 7.4.3 7.4.4 7.4.5 7.4.6 Application-Level Backup .................................................................................. Image-Level Backup ............................................................................................ Die Tücken von Images für die Datensicherung ....................................... Disaster Recovery ................................................................................................. Konsistenztypen .................................................................................................. Recovery Objectives ............................................................................................ 635 637 638 644 645 647 Die Wiederherstellung planen ...................................................................................... 649 7.5.1 7.5.2 Fallbeispiele ........................................................................................................... Fazit: Die Wiederherstellung planen ............................................................ 650 656 Windows Server-Sicherung ............................................................................................ 656 7.6.1 7.6.2 7.6.3 7.6.4 7.6.5 7.6.6 7.6.7 7.6.8 Neuerungen in Windows Server 2012 ........................................................... Einschränkungen ................................................................................................. Windows Server-Sicherung installieren ....................................................... VM-Sicherung einrichten .................................................................................. Wiederherstellung .............................................................................................. Überwachung ....................................................................................................... Backup innerhalb virtueller Maschinen ....................................................... Besonderheiten im Failover-Cluster .............................................................. 658 658 659 659 667 671 671 672 System Center Data Protection Manager 2012 SP1 .............................................. 672 7.7.1 7.7.2 672 673 6.10 7.5 7.6 7.7 Neue Funktionen in SCDPM 2012 SP1 ............................................................ Systemanforderungen ....................................................................................... 13 Inhalt 7.7.3 7.7.4 7.7.5 7.7.6 7.7.7 SCDPM 2012 installieren .................................................................................... Inbetriebnahme ................................................................................................... Virtuelle Maschinen sichern ............................................................................ Virtuelle Maschinen wiederherstellen ......................................................... Erweiterte Systemadministration .................................................................. 675 677 682 686 690 7.8 Ereignisprotokolle nutzen .............................................................................................. 696 7.9 Virtuelle Umgebungen überwachen ......................................................................... 702 7.9.1 Performanceüberwachung und -Tuning von Windows Server 2012 ......................................................................................... Leistungsüberwachung von Hyper-V-Hosts ............................................... Hyper-V mit System Center 2012 Operations Manager überwachen ........................................................................................................... Hyper-V mit Drittanbieter-Tools überwachen .......................................... Performance von Hyper-V-Systemen überwachen .................................. 705 706 707 VM-Monitoring .................................................................................................................... 707 7.10.1 7.10.2 7.10.3 Voraussetzung für das VM-Monitoring ....................................................... VM-Monitoring einrichten ............................................................................... VM-Monitoring überwachen ........................................................................... 708 708 710 PRO-Integration .................................................................................................................. 711 7.9.2 7.9.3 7.9.4 7.9.5 7.10 7.11 7.11.1 703 704 Anforderungen für die PRO-Integration in der SCOM-Umgebung ............................................................................................... Die PRO-Integration vorbereiten .................................................................... PRO-Integration für SCVMM 2012 .................................................................. PRO-Integration aktivieren ............................................................................... 712 712 714 716 7.12 Zusammenfassung ............................................................................................................. 720 8 Migration und Aktualisierung 721 8.1 Von Hyper-V 2.0 auf 3.0 umstellen ............................................................................ 721 8.1.1 8.1.2 Einzel-Hosts migrieren ...................................................................................... Failover-Cluster migrieren ................................................................................ 721 725 8.2 Von VMware vSphere zu Hyper-V migrieren ......................................................... 733 8.3 Den SCVMM aktualisieren .............................................................................................. 735 8.3.1 8.3.2 8.3.3 739 739 739 7.11.2 7.11.3 7.11.4 14 SCVMM-Datenbank vorbereiten .................................................................... SCVMM-Dienstkonto vorbereiten ................................................................. SCVMM-Server aktualisieren ........................................................................... Inhalt 8.3.4 8.3.5 8.4 8.5 Zu einem neuen SCVMM-Server migrieren ................................................ SCVMM-Agenten aktualisieren ...................................................................... 740 740 Microsoft Virtual Machine Converter Solution Accelerator ............................ 741 8.4.1 8.4.2 741 743 MVMC-Funktionen .............................................................................................. MVMC Automation Toolkit .............................................................................. Physische Server virtualisieren ..................................................................................... 744 8.5.1 8.5.2 8.5.3 Wann ist P2V nützlich? ...................................................................................... Wann und wie sollte ich P2V nicht nutzen? ............................................... Die Migration technisch umsetzen ............................................................... 744 746 747 8.6 Zusammenfassung ............................................................................................................. 755 9 Remotedesktopdienste 757 9.1 Bereitstellungsvarianten ................................................................................................. 757 9.2 Zielgruppen ........................................................................................................................... 759 9.3 Architektur ............................................................................................................................. 761 9.3.1 9.3.2 Kommunikation zwischen den Rollendiensten ........................................ Verschlüsselte Kommunikation ..................................................................... 763 767 Installation ............................................................................................................................. 767 9.4 9.4.1 Schnellstart-Installation einer sitzungsbasierten Desktopbereitstellung ....................................................................................... Schnellstart-Installation einer Bereitstellung virtueller Desktops ..... 769 772 Verwaltung ............................................................................................................................ 776 9.5.1 Mit dem Server-Manager administrieren ................................................... 777 9.5.2 Mit der PowerShell automatisieren .............................................................. 780 Desktop-Integration .......................................................................................................... 784 9.6.1 9.6.2 9.6.3 9.6.4 Die Verbindung einrichten ............................................................................... Persönliche Ressourcen einbinden ................................................................ Die Verbindung entfernen ................................................................................ Thin Clients ............................................................................................................ 784 788 789 790 Verbindungsprotokoll ...................................................................................................... 791 9.7.1 9.7.2 9.7.3 792 793 795 9.4.2 9.5 9.6 9.7 RemoteFX Adaptive Graphics .......................................................................... Multi-Stream ......................................................................................................... Die Grafikkarte virtualisieren .......................................................................... 15 Inhalt 9.7.4 9.7.5 9.7.6 USB umleiten ........................................................................................................ Multi-Touch ........................................................................................................... Verfügbarkeit ........................................................................................................ 796 796 797 Virtuelle GPUs konfigurieren ........................................................................................ 797 9.8.1 9.8.2 vGPUs für virtuelle Clients ................................................................................ Software-GPU für den Sitzungs-Host ........................................................... 797 800 9.9 Den Sitzungs-Host virtualisieren ................................................................................. 801 9.10 Best Practices für virtuelle Desktops ......................................................................... 803 9.11 Best Practices für den Virtualisierungs-Host .......................................................... 805 9.12 Lizenzierung .......................................................................................................................... 805 9.12.1 9.12.2 Lizenzierung der sitzungsbasierten Bereitstellung .................................. Lizenzierung der Bereitstellung virtueller Desktops ................................ 806 808 Zusammenfassung ............................................................................................................. 808 9.8 9.13 10 Finale und Ausblick 809 10.1 Lizenzierung für Hyper-V ................................................................................................ 810 10.1.1 10.1.2 810 812 10.2 Server: Das Betriebssystem .............................................................................. Applikationen: Lizenzmobilität ....................................................................... Die Fallbeispiele im fertigen Zustand ........................................................................ 813 10.2.1 10.2.2 Die A. Datum GmbH ........................................................................................... Die Contoso AG .................................................................................................... 813 815 10.3 Werkzeugkasten für Hyper-V ....................................................................................... 819 10.4 Hyper-V im virtuellen Testlabor ................................................................................... 820 10.5 Community und Quellen ................................................................................................. 823 Index ....................................................................................................................................................... 827 16 Index Index 00-15-5D...................................................................... 438 10GE 씮 10-Gigabit-Ethernet 10GE-Netzwerk mögliches Design............................................... 194 10-Gigabit-Ethernet ............................................... 187 1541................................................................................... 29 4K-Platte..................................................................... 415 5Nine............................................................................ 178 5nine Manager for Hyper-V................................... 99 99,999 Prozent Verfügbarkeit ........................... 279 A A. Datum GmbH Vorstellung .............................................................. 40 Abfrageinitiatorcomputer .................................. 242 Abrechnung nutzungsbasierte ............................................... 447 Absolute Bandbreiten-Reservierungsmodus ............. 192 Abstraktionsebene für virtuelle Switches ........................................ 457 Access Control List ................................................. 261 ACL 씮 Access Control List ACPI.............................................................................. 440 Active Directory ...................................................... 272 Active Directory Forest Recovery................. 653 Benutzerkonto wiederherstellen.................. 633 in einer VM ........................................................... 523 Schema................................................................... 693 vollständiger Ausfall ........................................ 653 wiederherstellen ................................................. 651 ADHD........................................................................... 478 ADK 씮 Windows Assessment and Deployment Kit Administration getrennte ............................................................... 275 Administrator mit Leseberechtigung ............ 578 Agent Datensicherung .................................................. 634 Aktiv-/Aktiv-Cluster .............................................. 291 Allgemeine Anwendung ...................................... 318 Allgemeiner Dienst................................................ 318 Allgemeines Skript................................................. 318 Ältere Netzwerkkarte ............................67, 396, 430 Always-on Database .............................................. 545 AMD Virtualization................................63, 106, 820 AMD-V 씮 AMD Virtualization Änderungsjournal .................................................. 678 Anforderung Datenwiederherstellung.........................631, 655 geschäftliche ...........................................................34 Angriffsfläche........................................................... 262 Anhalten VM............................................................................ 462 Anteil an Gesamtressourcen (CPU) ................. 407 Anwendung virtualisieren........................................................ 521 Anwendung 씮 Applikation Anwendungs- und Dienstprotokoll ................ 697 Anwendungsadministrator.......................578, 580 Anwendungspaket ................................................. 582 Anwendungsprofil ........................................582, 583 Anwendungsprotokoll ......................................... 697 Anwendungsskript................................................. 582 Anwendungsvirtualisierung.............................. 521 Anzeigename einer VM .......................................................394, 401 App Controller ...................................... 559, 587, 601 Appliance ................................................................... 214 Application Consistency...................................... 646 Application-Level Backup.................................... 635 Applikation Datensicherung .................................................. 634 Lizenz ...................................................................... 812 virtualisieren...............................................405, 520 App-V ........................................................................... 807 Arbeitsspeicher........................................................ 116 beim Start.....................................................122, 404 dynamischer ........................................................ 125 einer VM .......................................................394, 402 Puffer....................................................................... 126 statischer ............................................................... 125 überbuchen........................................................... 403 Umfang .................................................................. 126 Arbeitsspeicherpuffer........................................... 404 Arbeitsspeicherumfang ....................................... 404 Archivattribut 씮 Windows Server-Sicherung Aufgabenplaner....................................................... 335 Auftrag ........................................................................ 582 Ausfall Definition .............................................................. 281 vermeiden ................................................................33 827 Index Ausfall-Rechenzentrum....................................... 285 Ausfallsicherheitsplanung.................................. 651 Ausfallwahrscheinlichkeit .................................. 278 Ausfallzeit tolerierbare........................................................... 280 Ausführungskonto.....................258, 566, 569, 584 Auslagerung.............................................................. 118 Auslagerungsdatei ........................................115, 223 Authoritative Restore ........................................... 656 Automatische Startaktion................................... 402 Automatische Stoppaktion ................................ 402 AVHD(X)-Datei................................................478, 489 AZMan......................................................................... 270 Azman.msc................................................................ 270 Azure 씮 Windows Azure B B2D2T........................................................................... 695 Backup................................................................629, 722 Application-Level ............................................... 635 Ebene....................................................................... 634 Image-Level .......................................................... 637 Methode................................................................. 634 Backup-Server .......................................................... 651 Backup-Software ..................................................... 636 Ballooning ................................................................. 124 Bandbibliothek ........................................................ 695 Bandbreite auf virtuelle Netzwerke verteilen................. 192 Bandbreiten-Management .............. 364, 434, 574 Bandbreiten-Reservierung ................................. 190 Bandbreiten-Verwaltung..................................... 183 für eine virtuelle Netzwerkkarte .................. 434 Bandlaufwerk ...............................677, 678, 681, 692 Bare Metal............................................... 554, 555, 582 Bare-Metal-Hypervisor 씮 Hypervisor Baseboard Management Controller............... 610, 612, 614 Benutzerdichte ...............................................802, 804 Benutzerrolle.............566, 578, 579, 600, 601, 607 Berechtigung für VMConnect.................................................... 460 Bereitstellung virtueller Desktops................... 758 Best Practices Analyzer ................................. 74, 262 Best-Effort-Support................................................ 522 Bestmöglicher Knoten.......................................... 328 Bevorzugter Besitz ................................................. 291 BGInfo ......................................................................... 471 828 BI 씮 Business Intelligence Bibliothek....................554, 562, 582, 588, 599, 624 Bibliotheksfreigabe............................. 475, 578, 589 Bibliotheks-Server ............ 555, 557, 571, 589, 737 Biener-Haken, Cara ...................................................43 Bildschirmfoto......................................................... 463 Bildschirminhalt kippt nach links .................................................. 463 BIN-Datei.................................................................... 128 BIOS .............................................................................. 525 Einstellung ............................................................ 460 virtuelles ................................................................ 398 Bitlocker ..................................................................... 269 Blade-Server .............................................................. 533 Blech................................................................................35 Blockgröße von Festplatten ................................................... 415 Blockorientierter Speicher.................................. 420 Blockorientiertes Protokoll ................................ 215 Bluescreen bei der Live-Migration...................................... 410 BMC 씮 Baseboard Management Controller Boot from SAN ......................................................... 222 BPA 씮 Best Practices Analyzer Brand im Server-Raum ......................................... 650 Broadcom................................................................... 178 Budget für IT ............................................................. 279 Business Intelligence............................................. 544 C C64 ...................................................................................29 CAB 씮 Cabinet-Datei Cabinet-Datei............................................................ 499 Calista Technologies 씮 RemoteFX CAU 씮 Cluster Aware Updating CCR 씮 Failover-Cluster CentOS......................................................................... 511 CheckDisk .................................................................. 749 Checkpoint 씮 Snapshot Child Partition.............................................................72 Chkdsk......................................................................... 692 CIFS 씮 Common Internet File System Cisco Nexus 1000V ................................................ 178 Citrix ...................................................................759, 780 XenApp............................................................ 49, 780 XenServer ............19, 57, 61, 415, 553, 554, 572, 573, 584, 597, 610, 621, 625 XenServer 6.0....................................................... 625 XenServer 6.1 ................................... 47, 48, 49, 625 Index Client virtueller ................................................................ 129 Client-Zugriffspunkt.....................................319, 321 Cloning........................................................................ 472 Cloning-Prozess....................................................... 257 Cloud..........556, 566, 579, 584, 595, 596, 597, 608 Desktop-as-a-Service ...............................805, 806 Hosted .................................................................... 607 Private .................................................................... 607 Service Provider Licensing Agreement ..............................................805, 806 Software-as-a-Service....................................... 805 Cloud-Bibliothek..................................................... 588 Cloud-Kapazität....................................................... 596 Cluster aus VMs ................................................................. 522 hybrider Aufbau ................................................. 523 Cluster Aware Updating..........294, 330, 331, 336, 354, 365, 615 Cluster Bootstrapping........................................... 530 Cluster Continuous Replication (CCR) ........... 537 Cluster Name Object ............................................. 290 Cluster Node Weight ............................................. 336 Cluster 씮 Failover-Cluster Cluster Shared Volume ...... 48, 53, 290, 293, 297, 311, 320, 342, 348, 673, 683, 703, 727 v2 ................................................................................. 53 Cluster Shared Volume File System ................ 311 Cluster.exe........................................................300, 339 Cluster-Dienst .......................................................... 710 Clusterfähiges Aktualisieren 씮 Cluster Aware Updating Cluster-Knoten ........................................................ 541 Cluster-Migrationsassistent......................299, 729 CNO 씮 Cluster Name Object Codename Viridian................................................... 51 Committed Memory ............................................. 126 Common Internet File System................214, 346, 357, 678 Compliance-Management .................................. 554 COM-Port in einer VM ........................................................... 400 Compute-Cluster .................................................... 291 Computerkennwort............................................... 639 Computerkonto ...................................................... 639 Configuration Manager ..............................553, 694 Connectix ........................................................... 46, 414 Connectix Virtual PC................................................ 45 Contoso AG Vorstellung .............................................................. 42 Converged Fabric.................................................... 188 Converged Network...................208, 217, 251, 817 Copy on Write .......................................................... 636 Core 씮 CPU CP-40...............................................................................46 CPU Begrenzung........................................................... 408 Core.................................................................390, 405 für SQL Server ...................................................... 547 Kern ......................................................................... 405 Kompatibilität .................................................... 409 logische ......................................107, 114, 405, 704 Oracle Database ................................................. 549 Reserve ................................................................... 407 Ring.............................................................................64 Sockel ...................................................................... 390 Version ................................................................... 409 Virtualisierung .......................................................63 virtuelle ......................................107, 114, 406, 704 Crash Consistency .................................................. 645 Crawler SharePoint ............................................................ 551 Credential Security Support Provider ........... 344, 357, 568 CredSSP 씮 Credential Security Support Provider CSS 씮 Microsoft Customer Support Services CSV............................................................. 348, 658, 726 Netzwerk................................................................ 190 CSV 씮 Cluster Shared Volume CSVFS 씮 Cluster Shared Volume File System D DaaS 씮 Cloud DAG 씮 Database Availability Group DAS 씮 Direct Attached Storage Data Center Bridging....................................189, 208 Data Protection Manager ........254, 620, 672, 703 Agent-Koordinator............................................ 679 DPM 2010 .............................................................. 673 Hyper-V Express Full Backup......................... 683 Installation ........................................................... 677 Item Level Recovery .......................................... 689 Schutz-Agent............................678, 682, 684, 695 Schutzgruppe..............................................680, 681 Speicherplatzrechner........................................ 681 Speicher-Pool ....................................................... 691 Verwaltungskonsole ...................... 675, 679, 686 Vorbereitungs-Tool ........................................... 694 Wiederherstellungsassistent ......................... 686 829 Index Database Availability Group ..............44, 310, 538 Database Mirroring................................................ 545 Datacenter Edition Windows Server 2012 ........................................ 810 Dateien kopieren zwischen Host und VM .................................... 464 Dateiorientiertes Protokoll 씮 Protokoll Dateisystem NTFS ........................................................................ 234 ReFS ......................................................................... 234 VSS ........................................................................... 636 Datenaustausch Integrationsdienst ............................................. 441 mit einer VM ...............................................400, 463 Datenbank-Server..........................................543, 548 Datenbankwiederherstellung............................ 620 Datenkorruption..................................................... 655 Datensicherung....................................................... 629 braucht kein Mensch ........................................ 629 zwischendurch ....................................................... 38 Datenspeicher.......................................................... 209 Fallbeispiel ............................................................ 250 flexibler .................................................................. 229 Performance ........................................................ 220 Datenträger zwischen Host und VM austauschen ......... 465 Datenträger bearbeiten (Befehl) ....................... 419 Datenträger überprüfen (Befehl)...................... 420 Datenträgerbereinigungs-Tool ......................... 691 Datenverkehr trennen per VLAN................................................................ 193 Datenverlust............................................................. 630 maximal tolerierbarer ..................................... 648 Datenwiederherstellung...................................... 630 Endbenutzer ......................................................... 693 DCB 씮 Data Center Bridging dcpromo.exe............................................................. 644 Debian......................................................................... 515 Default Bandbreiten-Reservierungsmodus ............. 192 Demilitarisierte Zone...... 251, 259, 273, 567, 673 Deployment Image Servicing and Management .............................................. 496 Der Weg ist das Ziel................................................... 32 Desktopbereitstellung.......................................... 758 Device Specific Module ..................... 219, 244, 427 devmgr_show_nonpresent_devices .............. 754 DFS 씮 Distributed File System DFS-Namespaceserver.......................................... 318 DHCP Guard 씮 DHCP-Wächter DHCP 씮 Dynamic Host Configuration Protocol 830 DHCP-Server ....................................................264, 318 DHCP-Wächter......................................................... 439 Diagnosemöglichkeit............................................ 702 Dienstvorlage ........................................ 472, 582, 583 Differentiated Services Code Point ................. 365 Differenz-Festplatte......................................416, 417 Domänencontroller .......................................... 526 Differenzierung (Festplatte) ............................... 416 Dille, Nicholas .............................................................28 Direct Attached Storage ............ 49, 210, 243, 246, 305, 533 Disaster Recovery ..........................................644, 745 Disk2Vhd .................................................................... 748 Diskettenlaufwerk in einer VM ........................................................... 400 Disk-Image ................................................................ 637 Diskless Server ................................................222, 252 Diskpart .........................................................................95 DISM 씮 Deployment Image Servicing and Management Distributed File System...........................................44 Distributed Key Management.......................... 737, 738, 739, 740 Distributed Management Task Force ............. 447 Distributed Network Name ................................ 299 Distributed Resource Scheduling........................48 VMware.....................................................................47 DKM 씮 Distributed Key Management DMTF 씮 Distributed Management Task Force DMZ 씮 Demilitarisierte Zone DMZ-Server ............................................................... 260 DNN 씮 Distributed Network Name DO 씮 Dynamic Optimization Dokumentation Notwendigkeit..................................................... 651 Dom0..............................................................................61 Domäne Host als Mitglied ................................................ 272 separate ................................................................. 274 Domänencontroller aus der Domäne entfernen ............................ 652 physischer ............................................................. 530 Ressource............................................................... 531 virtualisieren........................................................ 523 wiederherstellen ................................................. 651 DOS..................................................................................28 Downtime.................................................................. 732 geplante ................................................................. 282 ungeplante............................................................ 282 Verringerung........................................................ 724 DPM 씮 Data Protection Manager Index DRS 씮 Distributed Resource Scheduling DSCP 씮 Differentiated Services Code Point DSM 씮 Device Specific Module Dynamic Host Configuration Protocol ........................................................439, 587 Dynamic Memory .....................114, 120, 125, 404, 537, 538, 539, 586 soziale Auswirkung ........................................... 124 SQL Server ............................................................. 545 Dynamic Optimization ..............................541, 575, 610, 625, 711 Dynamics 씮 Enterprise Resource Planning Dynamisch erweiterbare Festplatte.......416, 539 Dynamische MAC-Adresse ................................. 438 Dynamische Optimierung 씮 Dynamic Optimization Dynamischer Arbeitsspeicher...........82, 114, 404 E E/A-Virtualisierung mit Einzelstamm ... 64, 178, 180, 183, 436 Eildienst...................................................................... 280 Eingeschränkte Kerberos-Delegation............ 344, 345, 357, 568 Emulation ..................................................................... 62 Emulierte Netzwerkkarte .................................... 430 Emuliertes Gerät ........................................................ 71 Endbenutzer-Datenwiederherstellung.......... 693 Endpoint Protection.............................................. 306 Energiebedarf einer virtuellen Umgebung ............................... 35 Energieoptimierung 씮 Power Optimization Enlightenment.....................................................63, 65 Enterprise Resource Planning ........................... 544 Dynamics .............................................................. 544 SAP........................................................................... 544 Entwicklungslabor für Hyper-V........................................................... 820 Ereignis-ID................................................................. 701 Ereignisprotokoll .................................................... 696 ERP 씮 Enterprise Resource Planning ERP-System .................................................................. 37 Erweiterbarer Netzwerk-Switch........................ 178 Erweitern VHD-/VHDX-Datei ............................................ 419 Erweiterungs-Manager für Switche................. 575 Ethernet-Frame Maximalgröße .................................................... 188 Ethernet-Pool ........................................................... 457 Event Viewer 씮 Ereignisprotokoll Event-ID 씮 Ereignis-ID Exchange Datenbank ............................................................ 535 Datensicherung .................................................. 631 Server .............................................................532, 680 Server 2003........................................................... 534 Server 2007 ..................................................535, 537 Server 2010 ..................................................534, 537 Server 2013 ............................................................ 538 Server Lizenz ........................................................ 813 Exchange Edge-Server .......................................... 817 Export....................................................... 722, 724, 726 einer VM ................................................................ 488 virtuelle Maschine ............................................. 638 F Fabric ..................................... 573, 586, 624, 628, 740 Administrator...................................................... 578 Management .................................... 554, 566, 570 Failback ..............................................................289, 290 Failover ...........................................289, 318, 327, 328 Netzwerkkarte ..................................................... 189 Failover-Cluster ................ 206, 253, 293, 306, 353, 365, 537, 577, 586, 615, 672, 702, 725, 738 API............................................................................ 333 Cluster Name Object ......................................... 290 Cluster Shared Volume .................................... 290 Continuous Replication................................... 292 Datenträger.......................................................... 299 Dienst.............................................................294, 338 DLL ........................................................................... 319 Ereignis..........................................................325, 326 Funktionalität ..................................................... 289 Grenze..................................................................... 286 Heartbeat ...............207, 290, 307, 312, 316, 329 IP-Adresse.....................................................290, 327 keine Mehrheit .................................................... 310 Knoten .......... 289, 292, 294, 298, 301, 306, 307, 308, 311, 312, 314, 318, 327, 329, 334, 336, 338, 613, 614 Knoten- und Dateifreigabemehrheit.......... 310 Knoten- und Datenträgermehrheit ............ 309 Knotenmehrheit ................................................. 309 Kommunikation................................................. 312 Konfiguration...................................................... 304 löschen ................................................................... 726 Manager ................................................................ 314 maximale Anzahl Knoten..................................77 831 Index maximale Anzahl VMs ....................................... 77 Name....................................................................... 314 Parameter ............................................................. 340 Prüfbericht............................................................ 314 Quorum ........ 289, 294, 298, 307, 308, 311, 336 Registrierung ....................................................... 299 Ressource ........................................... 326, 337, 339 Rolle................ 289, 290, 306, 311, 318, 320, 328 Server ...................................................................... 289 Split Brain ............................................................. 307 Stimme ................................................................... 308 und Dynamic Memory..................................... 130 Update.................................................................... 721 Validierung........................................ 290, 302, 304 Validierungsassistent....................................... 301 Validierungsbericht .......................................... 304 Validierungstest ................................................. 303 verschachtelter ................................................... 282 Verwaltungskonsole ............293, 295, 324, 325, 326, 335, 688, 710 Voter .................................................... 289, 308, 335 Zeugendatenträger ........................ 307, 310, 316 Zeugenfreigabe ................................................... 308 Fall, Clara ............................................................. 40, 813 Fallbeispiele im fertigen Zustand .......................................... 813 Fallstudie....................................................................... 40 Fat Client .................................................................... 758 FC 씮 Fibre Channel FC-HBA........................................................................... 82 FCoE 씮 Fibre Channel over Ethernet Fehler Best Practices Analyzer....................................... 74 in einer Anwendung.......................................... 286 Festplatte defekte .................................................................... 231 Differenzierung..........................................416, 417 dynamisch erweiterbare ................................. 416 in einer VM ........................................................... 413 lokale ...................................................................... 211 mit fester Größe.................................................. 416 Pass-through ....................................................... 420 Festplatte voll........................................................... 489 Festplattendatei in einem VM-Snapshot .................................... 478 Fibre Channel .................... 209, 216, 300, 311, 425, 577, 677, 683 LUN in einer VM anbinden............................. 429 Fibre Channel over Ethernet .......... 189, 208, 216, 251, 300, 817 832 Fibre-Channel-Adapter......................................... 397 Fielmalz, Anke.............................................................40 File Transfer Protocol............................................ 214 Filesystem Consistency........................................ 646 Finn, Aidan ...................................................................31 Firewall 씮 Windows-Firewall Five-Nine .................................................................... 279 Flatrate für virtuelle Maschinen ................................... 812 Forefront Threat Management Gateway 2012 ....................................................... 180 Forefront TMG 씮 Forefront Threat Management Gateway 2012 Fragmentierung Dateisystem ......................................................... 417 Frame........................................................................... 117 Front-Firewall........................................................... 259 FSUTIl.EXE.................................................................. 323 FTP 씮 File Transfer Protocol Fünf Minuten Kerberos-Ticket ................................................... 527 Funktionsprofil............................583, 584, 586, 599 G Gast-Betriebssystem-Profil............. 474, 475, 579, 583, 584, 600 Gast-Cluster ........................................... 424, 522, 545 Gast-Cluster 씮 Guest Failover Clustering Gast-Teaming ........................................................... 440 Gateway ...................................................................... 576 GbE 씮 Gigabit-Ethernet Gelöschte VM importieren .......................................................... 493 GEM.................................................................................28 Geo-Cluster.......................................................291, 292 Geräte-Manager inaktive Geräte ................................................... 754 Geschäftsführung Verantwortung ................................................... 287 Geschäftsprozess ....................................34, 632, 648 Abhängigkeit von IT ......................................... 277 Geschwindigkeit Speichersystem ................................................... 210 Gewichtung Bandbreiten-Reservierungsmodus.............. 192 Gewissheit überprüfen ...............................................................39 Gigabit-Ethernet ..................................................... 187 Index Gleichwertiges Objekt........................................... 588 Globally Unique Identifier .................................. 472 einer VM ................................................................... 71 GPT 씮 GUID Partition Table Grenze .....................................................................76, 81 für virtuellen Computer (CPU) ...................... 407 Gröbner, Christian .................................................... 31 Group Managed Service Accounts................... 298 Group Policy Preferences.................................... 476 Gruppenrichtlinie .........................................272, 468 Guest Cluster ............................................................ 522 Guest Failover Clustering.................................... 545 GUID Partition Table ....................................587, 691 GUID 씮 Globally Unique Identifier H Hannover...................................................................... 29 Hardware Datenwiederherstellung ........................649, 654 einsparen.................................................................. 35 emulierte .................................................................. 81 Überwachung ...................................................... 702 Hardware Load Balancer...................................... 764 Hardware-Beschleunigung Netzwerkkarte..................................................... 434 Hardware-Profil........253, 474, 583, 585, 586, 620 Hardware-Topologie verwenden (NUMA).... 413 Hardware-Virtualisierung...................................... 63 HBA 씮 Host-Bus-Adapter Headcrash.................................................................. 281 Heartbeat ................................................................... 290 zwischen VM und Host ....................................... 65 Henne-Ei-Problem.................................................. 530 Herunterfahren VM............................................................................ 462 Herunterfahren des Betriebssystems Integrationsdienst ............................................. 440 Hierarchie Ressourcen-Pool ................................................. 454 High Availability VMware..................................................................... 47 Horizontales Skalieren .............299, 308, 317, 328 Host identifizieren ................................................. 470 Host-Bus-Adapter .......................219, 254, 304, 429 Host-Cluster.............................................................. 347 Hosted Cloud............................................................ 607 Host-Gruppe.................................566, 579, 610, 614 Hosting Mode .......................................................... 538 Host-Name auf dem VM-Desktop anzeigen .................... 471 Host-Profil .............................................. 583, 587, 599 Host-Server Name in einer VM anzeigen .......................... 470 weitere Dienste betreiben ............................... 531 wiederherstellen ................................................. 651 Host-Teaming .......................................................... 440 Hot-Add Memory ..........................................123, 545 Hot-Spare ................................................................... 232 HRL 씮 VM-Replikation HTTPS .......................................................................... 767 hv_ Treibermodule in Linux ................................... 512 Hybrid-Cluster ......................................................... 523 Hyper-Threading .......................... 81, 106, 114, 405 Hyper-V....................................................................... 766 Administration ohne Domäne ........................97 Administrator...................................................... 270 Express Full Backup........................................... 683 Installation auf USB-Stick .................................95 Integrationsdienst ............................................. 684 Lizenz .........................................................................92 Manager ...................................................................97 Monitor .................................................................. 706 Remoteverwaltung konfigurieren..................94 Replikatbroker..................................................... 318 Server-Konfiguration...........................................93 Switch ..................................................................... 261 Switch Extension ................................................ 178 Switch-Erweiterung...........................78, 269, 575 Switch-Erweiterung (maximale Anzahl)......82 Version 1.0................................................................45 Version 2.0 ...............................................................45 Version 3.0 ...............................................................45 VSS Writer ....................................................657, 684 Hyper-V Replica................................................ 53, 295 Hyper-V Server 2012 .................................................92 Hypervisor.................................................55, 180, 389 Bare Metal................................................................57 hosted ........................................................................58 Logical Processor ............................................... 704 Microkernel .............................................................61 monolithischer.......................................................60 nativer .......................................................................57 Partition................................................................. 705 Root Virtual Processor ..................................... 704 Typ 1............................................................................57 Typ 2 ...........................................................................58 Virtual Processor................................................ 704 Xen ..............................................................................46 833 Index I I/O Operations per Second .....220, 301, 311, 540 I/O-Last ....................................................................... 341 IBM Cambridge Scientific Center........................ 46 Icons für VM-Verbindungen erzeugen .................. 461 ID einer VM ............................................................... 490 IDE-Controller in einer VM ..................................................398, 413 IDS 씮 Intrusion Detection System IIS 씮 Internet Information Services ILR 씮 Item Level Recovery Image..................................................................524, 637 Datensicherung .................................................. 634 Probleme bei der Datensicherung............... 638 Image-Level Backup............................................... 637 ImDisk......................................................................... 466 Import ......................................................................... 724 einer VM .......................................................488, 490 VM in einen Cluster........................................... 351 Improvisation strukturierte......................................................... 288 Improvisieren nach einem Schaden......................................... 281 Infiniband.................................................................. 311 Initiator....................................................................... 218 Initiatorcache ........................................................... 242 initram ........................................................................ 518 Inkonsistenz Active Directory.................................................. 524 In-Place-Update....................................................... 735 In-Place-Upgrade .................................................... 725 Input 64 ......................................................................... 29 Installationsmedium in einer VM ........................................................... 396 Installationsreihenfolge Hyper-V-Cluster .................................................. 347 Integration Component 씮 Integrationsdienst Integration Service 씮 Integrationsdienst Integrationsdienst .............65, 401, 430, 440, 657, 684, 753 aktualisieren ........................................................ 444 Datenaustausch ................................................. 441 für Linux ................................................................ 510 Herunterfahren des Betriebssystems ......... 440 installieren............................................................ 462 Linux ................................................................ 66, 442 Sicherung (Volume-Momentaufnahme) .. 442 Takt.......................................................................... 442 834 Zeitsynchronisation .......................................... 440 Zeitsynchronisierung........................................ 528 Integritätsmonitor ................................................. 575 Intel Virtualization Technology........63, 106, 820 Intel VT 씮 Intel Virtualization Technology Internet Information Services..................606, 763 Internet SCSI 씮 iSCSI Internetinformationsdienste 씮 Internet Information Services Intrusion Detection System ............................... 259 Intrusion Prevention System ...................259, 264 IOPS 씮 I/O Operations per Second IPS 씮 Intrusion Prevention System IPsec ............................................................................. 477 IPsec Task Offloading 씮 IPsec-Task-Abladung IPsec-Task-Abladung .......................... 183, 436, 576 IPv6......................................................................375, 427 Irrtum gefährlicher .............................................................38 iSCSI..................... 188, 216, 300, 311, 425, 677, 683 Initiator.........................................................218, 426 LUN in einer VM anbinden............................. 426 Netzwerkverkehr ................................................ 238 Target................................................... 218, 340, 427 Target als Cluster ............................................... 343 Target in Windows Server 2012 .................... 237 ISO-Datei ...........................................................572, 588 zum Datenaustausch ....................................... 466 ISO-Image .........................................................253, 257 Item Level Recovery .....................................683, 689 iX (Zeitschrift)..............................................................29 J JBOD 씮 Just a Bunch of Disks Jetzt-Stand VM-Snapshot ....................................................... 481 Journal......................................................................... 678 Jumbo Frame in Linux-VM.......................................................... 511 Just a Bunch of Disks ....................................211, 341 K Kaczenski, Nils ............................................................29 Kapazitätsplanung ................................................. 802 Kappen, Jan...................................................................30 Katastrophe............................................................... 644 Index KCD 씮 Eingeschränkte Kerberos-Delegation Keine Mehrheit nur Datenträger ................................................. 310 Kennwort Computer .............................................................. 639 Kerberos .................................................. 273, 357, 568 Protokoll ................................................................ 527 Kerberos Constrained Delegation 씮 Eingeschränkte Kerberos-Delegation Kern 씮 CPU Kernel für Linux kompilieren ...................................... 516 Kernprozess ................................................................. 21 Kestel, Sebastian ........................................................ 30 Key/Value Pair Exchange .................................... 441 Klonen......................................................................... 474 Domänencontroller .......................................... 526 Knoten- und Dateifreigabemehrheit.............. 310 Knoten- und Datenträgermehrheit ................ 309 Knotenmehrheit ..................................................... 309 Knowledge Worker 씮 Zielgruppe Köln................................................................................. 29 Kompatibilität von CPUs ............................................................... 409 Kompatibilitätseinstellung ................................ 586 Kompilierung eines Linux-Kernels ................. 516 Komplexität der Virtualisierung ............................................... 33 IT-Netzwerk .......................................................... 284 Komprimieren VHD-/VHDX-Datei ............................................ 419 Konfiguration einer VM exportieren........................................ 488 Konfigurationsanbieter ....................................... 580 Konfigurationsfehler ............................................ 655 Konsistenz................................................................. 641 Datenbank ............................................................ 636 Datensicherung .................................................. 638 systemübergreifend .......................................... 649 Konsistenzprüfung ................................................ 680 Konsistenztyp .......................................................... 645 Konsolenverbindung ............................................ 459 Kontextwechsel....................................................... 117 Konvertieren VHD-/VHDX-Datei ............................................ 419 Konzept für Ausfallsicherheit ......................................... 287 Kopieren einer VM ................................................................ 492 Korruption von Daten .......................................... 655 Kosten sparen .............................................................33 Kurzzeitspeicher ............................................677, 681 KVM.............................................................................. 821 L LACP 802.3ad ...............................................................49 Langzeitspeicher ............................................677, 695 Lastenausgleich ..............................................333, 610 Lastenausgleichsmethode .................................. 575 Lastenausgleichsmodul ..............................574, 597 Lastverteilung Netzwerkkarte ..................................................... 189 Layer-2-Switch.......................................................... 190 LCPU 씮 Logische CPU Legacy-Netzwerkadapter .............................. 67, 705 Leistungsindikator ................................................. 330 Leistungsklasse........................................................ 804 Linux in einer VM ........................................................... 510 Integrationsdienst ...................................... 66, 442 Troubleshooting in Hyper-V.......................... 518 Live-Migration .....................53, 207, 295, 312, 317, 322, 331, 337, 353, 354, 364, 533, 568, 610, 611, 727 Grenze........................................................................37 Netzwerk................................................................ 190 Speichermigration .................353, 360, 361, 362 vSAN beachten .................................................... 429 Lizenzierung ............................................................. 810 Applikation........................................................... 812 benutzerbezogene.............................................. 806 endgerätebezogene ........................................... 806 Virtual Desktop Access .................................... 808 Lizenzmobilität ....................................................... 812 Load Balancer ........................................................... 817 Logical Unit Number...... 216, 218, 316, 320, 340, 344, 421, 429, 533 in einer VM ........................................................... 424 Logische CPU ............................................................ 405 Logischer Switch ..................................................... 575 Logisches Netzwerk ............................ 574, 592, 597 vom physischen Netzwerk entkoppeln...... 190 Löschmethode ......................................................... 264 LUN 씮 Logical Unit Number Lüscher, Michel...........................................................31 Lync .............................................................................. 131 835 Index M MAC-Adresse ...................................................117, 722 dynamische .......................................................... 438 einer virtuellen Netzwerkkarte..................... 437 MAC-Adress-Pool.................................................... 574 Mailbox-Rollen-Kalkulator ................................. 540 Mailserver wiederherstellen ................................................. 633 Mainframe.................................................................... 46 Maintenance Host.................................................. 503 Malware ...................................................................... 650 Management OS 씮 Management-Betriebssystem Management Pack.................................................. 705 Katalog .................................................................. 715 Management-Betriebssystem .............................. 67 Netzwerk................................................................ 190 Mandantenadministrator................................... 578 Mandantenfähigkeit ............................................. 596 MAP 씮 Microsoft Assessment and Planning Toolkit Master Boot Record ......................................587, 691 Maurer, Thomas......................................................... 31 Maximales RAM.............................................121, 404 Maximalwert............................................................... 76 MBR 씮 Master Boot Record MBSA 씮 Microsoft Baseline Security Analyzer MDOP 씮 Microsoft Desktop Optimization Pack Mean Time Between Failures............................. 283 Mehrheit keine Mehrheit .................................................... 310 Knoten.................................................................... 309 Knoten und Dateifreigabe.............................. 310 Knoten und Datenträger ................................ 309 Memory Buffer ...................................................................... 126 Pressure.................................................................. 124 Weight .................................................................... 126 memoryreserve....................................................... 115 Messung von VM-Ressourcen .......................................... 457 Metering............................................................447, 457 Metrik zur Abrechnung der VM-Nutzung............... 448 Microsoft Assessment and Plannung Toolkit ............. 311 Baseline Security Analyzer ............................. 262 Customer Support Services ............................ 301 Desktop Optimization Pack.................... 50, 807 836 Dynamics .............................................................. 544 Enterprise Desktop Virtualization .................50 Exchange ............................................ 130, 266, 689 Exchange Server 2007 ...................................... 308 Forefront Threat Management Gateway 2010 .................................................................... 267 Forefront Unified Access Gateway 2010... 267 Message Analyzer .....................................184, 186 SharePoint ................................550, 673, 680, 689 SQL Server .... 131, 317, 557, 558, 559, 619, 689 SQL Server Management Pack...................... 712 Virtual PC ......................................... 46, 50, 59, 414 Virtual Server..........................................................58 Virtual Server 2005 ........................................... 521 Virtual Server 2005 R2 ............................535, 737 Virtual Server 2005 R2 SP1..........................45, 51 Windows Server 2012 Hyper-V .........................47 Microsoft-Update-Datei ....................................... 499 Mindest-Bandbreite............................................... 188 Minimale Server-Benutzeroberfläche............ 107 Minimales RAM..............................................121, 404 Mirror .......................................................................... 231 Möglicher Besitzer.................................................. 291 Momentaufnahme 씮 Snapshot Most Valuable Professional ...................................28 Mountpoint .............................................................. 235 MPIO 씮 Multipfad-E/A MSA 씮 Microsoft Message Analyzer MSI-Paket ................................................................... 181 MSU 씮 Microsoft-Update-Datei MTBF 씮 Mean Time Between Failures Multihomed DC....................................................... 532 Multipath I/O 씮 Multipfad-E/A Multipfad-E/A ...........196, 208, 219, 240, 243, 250 Multi-Site-Cluster ................................................... 335 MVP 씮 Most Valuable Professional N N_Port ID Virtualization.........................................82 Name einer VM ................................................................ 401 Namenskonvention für Netzwerkkarten ........................................... 469 für Ressourcen-Pools ........................................ 453 NAS 씮 Network Attached Storage NDIS 씮 Network Device Interface Specification NDMP 씮 Network Data Management Protocol Nested Virtualization............................................ 821 netlogon ..................................................................... 642 Index Network Attached Storage .................49, 210, 214, 243, 344, 678, 817 Network Data Management Protocol ........... 425, 634, 645 Network Device Interface Specification ....... 178, 179, 181, 184, 575 Network File System..............................48, 214, 678 Network Load Balancing................... 574, 575, 597 Network Time Protocol ........................................ 527 Netzwerk Datenverkehr messen....................................... 449 Fallbeispiel ............................................................ 207 iSCSI......................................................................... 238 PVLAN........................................................................ 79 Trace........................................................................ 186 Virtualisierung....................................................... 79 Netzwerkanmeldedienst ..................................... 641 Netzwerkfreigabe.................................................... 688 Netzwerkkarte ältere ................................................................ 67, 430 Bandbreiten-Verwaltung ................................ 434 benennen............................................................... 469 dimensionieren ................................................... 432 einrichten in einer VM ..................................... 433 emulierte ............................................................... 430 Hardware-Beschleunigung ............................ 434 im Management OS .......................................... 188 in Debian einrichten ......................................... 515 in einer VM ........................................ 395, 396, 430 MAC-Adresse........................................................ 437 maximale Anzahl ................................................. 82 synthetische .................................................. 67, 430 Teaming........................................................305, 575 überbuchen .......................................................... 432 Netzwerknamenressource.................................. 290 Netzwerkstandort................................................... 574 Netzwerkverbindung interne zwischen Host und VM .................... 464 Netzwerkverkehr separieren ............................................................. 190 Neu starten VM............................................................................ 462 Neumann, Daniel....................................................... 31 NEWSID....................................................................... 472 NFS 씮 Network File System NIC-Teaming............................................................. 206 NIC-Teamvorgang in einer VM ........................................................... 439 NLB 씮 Network Load Balancing Node Drain ................................................................ 336 Node Vote Weight .................................................. 335 None Bandbreiten-Reservierungsmodus.............. 192 Non-Uniform Memory Access .................127, 411 Notfall-Rechenzentrum ....................................... 815 NPIV 씮 N_Port ID Virtualization NT 4.0 Prozessorkompatibilität ................................. 411 NTFS 씮 Dateisystem NTP 씮 Network Time Protocol NUMA 씮 Non-Uniform Memory Access O Objektermittlung.................................................... 706 Offline Datenträger.......................................................... 422 OOBE 씮 Out of the Box Experience OpenFlow-Switch.................................................... 178 Operations Manager....... 307, 553, 580, 693, 702, 705, 710 Management Pack ...................................307, 693 Root Management Server............................... 712 Verwaltungskonsole ......................................... 713 Oracle Support................................................................... 548 VirtualBox................................................................59 Oracle Database....................................................... 548 Ressource............................................................... 549 Orchestrierung ........................................................ 615 OU-Struktur .............................................................. 272 Out of the Box Experience .................................. 473 Overcommit 씮 Überbuchen P P2V.........................................................39, 52, 554, 590 alte Hardware ..................................................... 744 DHCP....................................................................... 754 für Domänencontroller ..........................525, 746 Offline ..................................................................... 748 Online ..................................................................... 747 Physical-to-virtual-Migration..........................39 USB........................................................................... 746 verschlüsseltes Laufwerk ................................ 751 Pacifica ...........................................................................63 Packet .......................................................................... 117 Pagefile........................................................................ 223 Paging.......................................................................... 118 Paravirtualisierung .....................................62, 64, 72 837 Index Parent Partition...................................................61, 67 Parität.......................................................................... 231 Partition ........................................................................ 46 Child Partition........................................................ 72 Festplatte............................................................... 223 Parent Partition..................................................... 67 Partitionsstil GPT......................................245, 246 Virtualisierung....................................................... 63 Pass-through Disk ............................... 225, 355, 420 Export einer VM.................................................. 489 Passthrough Storage 씮 Pass-through Disk Patch-Strategie......................................................... 253 PCI Express................................................................ 436 PDC-Emulator .................................................527, 530 Peek-&-Poke-Poster .................................................. 29 Performance and Resource Optimization... 296, 581, 737 Performance Baseline........................................... 704 Perimeter-Netzwerk .....................................273, 567 Persistenz-Modus................................................... 575 Physical to Virtual 씮 P2V Physical-to-virtual-Migration 씮 P2V Physische Festplatte in einer VM ........................................................... 420 PKI 씮 Public Key Infrastructure Platz, Dennis ...................................................... 43, 813 Plug-in......................................................................... 334 PMADSchemaExtension...................................... 694 PO 씮 Power Optimization Port ACL...................................................................... 268 Port-Adresse virtueller Fibre-Channel-HBA........................ 429 Port-Gruppe .............................................................. 621 Port-Klassifizierung......................................575, 597 Port-Profil .................................................................. 576 systemeigenes ..................................................... 576 Port-Spiegelung..............................................184, 185 auf einem virtuellen Switch ........................... 439 Power and Resource Optimization Funktion ................................................................ 706 Integration ........................................ 714, 716, 719 Power Optimization .......................... 555, 575, 610, 612, 614, 625 Power User 씮 Zielgruppe PowerShell.................................................23, 181, 659 Administration von Hyper-V ........................... 84 Einstieg...................................................................... 85 Export-Skript........................................................... 84 Get-Help.................................................................... 87 Intellisense............................................................... 86 838 ISE................................................................................85 Skript..........................................................................91 Übersicht der Commandlets.............................92 Update.......................................................................87 Präsentationsvirtualisierung............................. 757 Preboot Execution Environment...........430, 571, 572, 587, 628 Primordial Ressourcen-Pool ................................................. 454 Speicher-Pool ....................................................... 232 Priorität von VM ................................................................... 407 Private Cloud ..................................................... 25, 607 PRO 씮 Performance and Resource Optimization Projektablauf ...............................................................21 Projektpraxis ...............................................................32 Projektziel.....................................................................33 Protected Mode ..........................................................63 Protokoll dateiorientiertes................................................. 214 Provisionierung ...................................................... 474 Prozentwert für Verfügbarkeit.......................... 279 Prozess ........................................................................ 117 Prozessor in einer VM ........................................................... 405 Prozessorarchitektur............................................. 688 Prozessorkompatibilität .............................354, 409 Prozessorversion .................................................... 409 PRTG Network Monitor........................................ 706 Prüfpunkt 씮 Snapshot Public Key Infrastructure .................................... 605 PXE 씮 Preboot Execution Environment Q Quality of Service (QoS) 씮 BandbreitenManagement Quick-Migration.............................................337, 539 Quorum ................................................... 250, 348, 727 Quote ........................................................................... 600 R RAC 씮 Real-Application Cluster Rachfahl, Carsten .......................................................31 RADC 씮 RemoteApp- und DesktopVerbindung Index RAID Alternative............................................................ 230 für RAM.................................................................. 123 Konfiguration...................................................... 212 Level 1.............................................................231, 310 Level 5 ..................................................................... 231 RAM.............................................................................. 116 tatsächlicher Bedarf.......................................... 133 Random I/O .............................................................. 547 Raw Device Mapping............................................. 226 RCO 씮 Recovery Consistency Objective RDMA 씮 Remote Direct Memory Access RDP 씮 Remote Desktop Protocol, Remotedesktop-Protokoll RDS CAL Per Device 씮 Lizenzierung RDS CAL Per User 씮 Lizenzierung RDS CAL 씮 Remote Desktop Services Client Access License RDS 씮 Remote Desktop Services Read-Only Domain Controller .................298, 651 Real-Application Cluster ...................................... 549 Recovery Methode................................................................. 634 Szenario ................................................................. 649 Recovery Consistency Objective .............647, 648 Recovery Objective ................................................ 647 Recovery Point Objective ...........................647, 648 Recovery Time Actual ..................................647, 648 Recovery Time Objective..................................... 647 Red Hat ....................................................................... 511 Redirected I/O.......................................................... 342 Redo-Log .................................................................... 549 Redundant Array of Independent Disks 씮 RAID Redundanz ................................................................ 278 problematische ................................................... 283 standortübergreifende..................................... 815 Redundanzkonzept................................................... 43 Redundanztyp Storage Space ...................................................... 231 ReFS 씮 Reliable File System Regelwerk zur Konfiguration ................................................. 74 Relationale Datenbank......................................... 635 Relative Gewichtung (CPU)................................. 407 Reliable File System ............................................... 673 Remote Desktop...................................................... 761 aktivieren in einer VM...................................... 468 Lizenzierung................................................766, 805 Remote Desktop Protocol ................................... 464 Remote Desktop Services.................................... 557 und Dynamic Memory..................................... 130 Remote Desktop Services Client Access License...........................................................766, 806 benutzerbasierte ................................................ 766 endgerätebasierte.............................................. 766 Remote Direct Memory Access......................... 297 Remote Server Administration Tools............. 557 Remote-Aktualisierung........................................ 332 RemoteApp ......................................................758, 783 Funktionsweise ................................................... 763 RemoteApp- und Desktopverbindung .......... 784 Remotedesktopdienst........................................... 757 Bereitstellung virtueller Desktops ............... 772 Gateway................................................................. 765 Historie................................................................... 759 Schnellstart-Installation ................................. 768 Sitzungsbasierte Desktopbereitstellung ... 769 Sitzungs-Host ...................................................... 765 Verbindungs-Broker.......................................... 764 Virtualisierungs-Host....................................... 765 WebAccess............................................................. 763 Remotedesktop-Gateway .................................... 762 Remotedesktop-Lizenzierung ........................... 762 Remotedesktop-Protokoll.......266, 464, 761, 791 virtuelle Kanäle................................................... 791 RemoteFX .........................................................354, 791 3D-Grafikkarte .................................................... 397 Adaptive Graphics ............................................. 792 Contact Rectangle ............................................. 796 Multi-Touch.......................................................... 796 Relative Timing................................................... 796 Touch Frames ...................................................... 796 USB Redirection .................................................. 796 Verfügbarkeit....................................................... 797 vGPU ....................................................................... 795 RemoteFX Adaptive Graphics 씮 RemoteFX Remoteserver-Verwaltungstools (RSAT)....... 103 repadmin.................................................................... 642 Replay-Angriff.......................................................... 527 Replikat SAN-basiertes....................................................... 637 Replikation Active Directory.................................................. 524 des Active Directorys ........................................ 640 Reserve für virtuellen Computer (CPU)......... 407 Ressource Maximalwerte in einer VM ............................ 391 Ressourcenabhängigkeit ..................................... 290 Ressourcengruppe.................................................. 290 Ressourcen-Pool...................................................... 447 einrichten .............................................................. 452 VMware.....................................................................48 839 Index Ressourcentyp in einem Ressourcen-Pool .............................. 447 Restore ...............................................................629, 655 Reverse Proxy .......................................................... 817 Risikoplanung .......................................................... 651 RODC 씮 Read-Only Domain Controller Rogue DHCP Server ............................................... 439 Rogue Router............................................................ 439 Rollback ...................................................................... 649 Rolleninhaber .......................................................... 329 Root Domain ............................................................ 653 Root Partition........................................................... 705 Router Guard 씮 Router-Wächter Router-Wächter ....................................................... 439 RPO 씮 Recovery Point Objective RSAT 씮 Remote Server Administration Tools RTA 씮 Recovery Time Actual RTO 씮 Recovery Time Objective S SaaS 씮 Cloud Sammlung ................................................................. 764 Sitzung ................................................................... 764 virtueller Desktops ............................................ 764 SAN 씮 Storage Area Network SAP 씮 Enterprise Resource Planning SAS 씮 Serial Attached SCSI SATA 씮 Serial ATA SBC 씮 Server-Based Computing Scale-Out File Server.....................................308, 346 SCC 씮 Single Copy Cluster SCCM 씮 Configuration Manager SCDPM 씮 System Center 2012 Data Protection Manager Schaden für das Unternehmen ....................................... 281 Schadensszenario................................................... 632 Schattenkopie ....................................... 387, 636, 656 Schwenk des Rechenzentrums ......................... 285 SCOM 씮 Operations Manager SCR................................................................................ 537 Screenshot einer VM ................................................................ 463 SCSI............................................................................... 292 Controller in einer VM .................. 396, 399, 413 SCVMM 씮 System Center 2012 Virtual Machine Manager SCVMM 씮 Virtual Machine Manager SCW .....................................................................254, 262 840 Second Level Address Translation ..........101, 106 Second Level Paging .....................................118, 127 Security Configuration Editor ........................... 254 Security Identifier................................ 256, 472, 643 Selbst signiertes Zertifikat .................................. 605 Selbstaktualisierung.............................................. 332 Self-Service Benutzer........................................................578, 588 Benutzergruppe .................................................. 606 Benutzerrolle...............................................587, 600 sepago ............................................................................28 Sequential Write I/O.............................................. 547 Serial ATA..........................................................106, 310 Serial Attached SCSI ............................ 106, 300, 310 Server Cloning.......................................................... 255 Server Message Block ...... 112, 214, 477, 678, 688 SMB 3.0............................. 252, 297, 323, 673, 727 Server Virtualization Validation Program .............................................. 522, 535, 544 Server-Applikation Lizenz ...................................................................... 812 Server-Ausfall ........................................................... 630 Server-Based Computing.............................. 28, 758 Server-Core-Installation....................................... 107 Server-Manager ..............................................107, 312 Server-Virtualisierung Vor- und Nachteil..................................................35 Service Level Agreement ..................................... 680 Setup ............................................................................ 722 sFlow ............................................................................ 178 SFTP 씮 Simple File Transfer Protocol Shared Nothing Live-Migration...............320, 724 Shared Nothing Live-Migration 씮 LiveMigration Shared-SAS ................................................................ 341 SharePoint ................................................................. 673 in einer VM ........................................................... 550 Ressource............................................................... 550 Support................................................................... 550 SharePoint 씮 Microsoft Shortcut für VM-Verbindungen erzeugen .................. 461 Sicherheitsprotokoll.............................................. 697 Sicherung (Volume-Momentaufnahme) Integrationsdienst ............................................. 442 Sicherungsagent ..................................................... 636 SID 씮 Security Identifier Silje, Peter......................................................................41 Silverlight................................................................... 607 SIM 씮 Windows System Image Manager Simple File Transfer Protocol............................. 622 Index Simultask ...................................................................... 46 Single Copy Cluster................................................ 537 Single Point of Failure..................................254, 308 Single Sign-on .......................................................... 272 Single-Root I/O Virtualization 씮 E/AVirtualisierung mit Einzelstamm Sitter, Till ....................................................................... 40 Sitzungsbasierte Desktop-Bereitstellung ..... 758 Sitzungsbasierter Desktop.................................. 758 Sitzungs-Host..................................................762, 765 Sitzungssammlung.......................................764, 782 Sitzungssammlung 씮 Sammlung Skalieren horizontales .............................299, 308, 317, 328 SLA 씮 Service Level Agreement SLAT 씮 Second Level Address Translation Small Business Server ........................................... 131 Smart Paging ...................................................126, 401 SMB 씮 Server Message Block SMI-S 씮 Storage Management Initiative – Specification SMP 씮 Storage Management Provider Snapshot .....................353, 477, 539, 601, 658, 722 anwenden ............................................................. 482 Checkpoint............................................................ 477 Dateigröße............................................................ 484 Datensicherung .................................................. 634 einer VM ......................................................... 37, 477 entfernen ............................................................... 485 exportieren ..................................................487, 489 Name....................................................................... 480 Prüfpunkt .....................................................477, 601 SAN-basierter....................................................... 637 virtuelle Maschine ............................................. 637 VM............................................................................ 462 zurücksetzen ........................................................ 482 zusammenführen............................................... 486 SoC 씮 System-on-a-Chip Sockel........................................................................... 405 Lizenzierung pro................................................. 811 SOFS 씮 Scale-Out File Server Soft Partitioning...................................................... 548 Software Assurance ............................................... 813 Software-VSS-Provider ......................................... 683 Solid State Disk ........................................................ 106 Spaghetticode ............................................................. 29 Sparziel .......................................................................... 33 Speicher zentraler ................................................................ 210 Speicherbedarf des Betriebssystems .............. 801 Speicher-Cluster...................................................... 340 Speichergerät Vorteil ..................................................................... 236 Speicherkapazität Host-Server ........................................................... 210 Speicherklassifizierung ........................................ 599 Speichern VM............................................................................ 462 Speichernetzwerk mit 10GE im Host-Server ................................. 196 Speicherort für die Smart-Paging-Datei............................ 401 für Snapshot-Datei ............................................ 401 Speicherpfad............................................................. 227 einer VM ................................................................ 394 Speicher-Pool .................... 212, 228, 230, 297, 311, 340, 341, 691 RAM ......................................................................... 120 Speicherseite ............................................................ 118 Speichersystem Komplettkopie .................................................... 645 Spiegel ......................................................................... 231 SPLA 씮 Cloud Split Brain .........................................................208, 307 SPoF 씮 Single Point of Failure SQL Server...................317, 543, 557, 558, 559, 619 Dynamic Memory .............................................. 545 Support................................................................... 544 SQL Server 2012........................................................ 673 Lizenz ...................................................................... 813 SQL Server Core Library ....................................... 714 SQL Server 씮 Microsoft SQL Server-Profil ............................................583, 587 squeeze (Debian)..................................................... 515 SR-IOV 씮 Single-Root I/O Virtualization SSD 씮 Solid State Disk Standard Edition Windows Server 2012 ........................................ 810 Standby-Cluster....................................................... 291 Starten VM............................................................................ 462 Startreihenfolge in einer VM ........................................................... 398 Startvorgang einer VM beobachten ....................................... 460 Stolperfalle ...................................................................36 Storage ...............................................................210, 340 Storage Area Network .... 210, 215, 254, 300, 301, 305, 307, 310, 311, 320, 344, 397, 533, 555 Datensicherung .................................................. 634 Datenträger in einer VM ................................. 423 virtuelles ................................................................ 426 841 Index Storage Management Initiative – Specification ........................................................ 577 Storage Management Provider......................... 577 Storage Space 씮 Speicher-Pool Storage-Controller.................................................. 300 Storage-Management ..................................554, 555 Storage-Migration ..................................................... 53 Storge Area Network ............................................. 305 Strg + Alt + Ende .............................................462, 463 Strg + Alt + Entf........................................................ 463 Strom sparen ............................................................... 33 Stromversorgung Ausfall .................................................................... 650 Stromzähler .............................................................. 449 Subject Alternate Name ....................................... 606 Support Best Practices Analyzer....................................... 74 für Cluster ............................................................. 522 für virtuelle Umgebung ...................................... 37 Oracle Database................................................. 548 SharePoint ............................................................ 550 SQL Server ............................................................. 544 Support-Policy für virtuelle Umgebungen .............................. 521 SVVP 씮 Server Virtualization Validation Program Switch Layer 2 ....................................................................... 78 Switch-Erweiterung ............................................... 182 Synchronisierungs-Engine ................................. 684 Synthetische Netzwerkkarte .............................. 430 Synthetisches Gerät.................................................. 72 Sysinternals .............................................................. 471 Sysprep ...........................................256, 472, 473, 775 System Center 2012 App Controller........................... 45, 559, 587, 601 Configuration Manager ............... 501, 553, 694 Data Protection Manager .......... 254, 542, 620, 672, 673, 703 Endpoint Protection.......................................... 306 Operations Manager ...........307, 553, 580, 693, 702, 705, 710, 712, 713 Operations Manager (SCOM)....................45, 53 Orchestrator............................................................ 46 Service Manager und System Center Orchestrator....................................................... 46 Virtual Machine Manager.............53, 253, 254, 296, 333, 474, 501, 541, 553, 673, 703, 712, 714, 717 842 System Center Virtual Machine Manager 2007 ........................................................52 System Center Virtual Machine Manager 2008 R2 ............................................... 555 System State ....................................................651, 653 Systemadministration 씮 Zielgruppe Systemeigenes Port-Profil................................... 576 systeminfo................................................................. 101 System-on-a-Chip ................................................... 792 Systemprotokoll...................................................... 696 Systemstate Active Directory.................................................. 524 Systemvorbereitungsprogramm ..................... 472 Systemzeit ................................................................. 440 T Tablespace ................................................................. 549 Takt Integrationsdienst ............................................. 442 Tape-Library.............................................................. 645 Target........................................................................... 218 Task Worker 씮 Zielgruppe Tastaturpuffer .......................................................... 463 Teaming Netzwerkkarte ..................................................... 189 Terminal-Dienst .............................................130, 759 Testlabor für Hyper-V ........................................................... 820 Text aus Zwischenablage eingeben................. 463 Thin Provisioning.......................223, 232, 417, 425 Thread ......................................................................... 117 TLS/SSL...............................................................765, 767 TMG 씮 Forefront Threat Management Gateway 2012 Toaster......................................................................... 214 Tombstone Recovery ............................................ 655 Tool Convert-WindowsImage.ps1 .......................... 494 dism ...................................................... 496, 499, 509 dism /Apply-Image............................................ 496 dism /Apply-Unattend ..................................... 509 dism /Enable-Feature ....................................... 499 dism /Get-ImageInfo ........................................ 496 dism /Get-PackageInfo.................................... 500 dism /Mount-Image....................... 496, 499, 509 dism /Unmount-Image ................ 496, 499, 509 PsExec ..................................................................... 502 Sysprep ..........................................................508, 509 Index SysPrep /Mode .................................................... 509 VM Services Tool ................................................ 501 WIM2VHD ............................................................. 495 TPM 씮 Trusted Platform Module Transactional Consistency.................................. 646 Transaktion......................................................640, 646 Transaktionsprotokoll SQL Server ............................................................. 547 Tree (Active Directory) ......................................... 653 Trusted Platform Module.................................... 269 U Überbuchen Arbeitsspeicher ................................ 118, 127, 403 Speicherplatz im Storage Space ................... 233 Überprovisionierung ............................................... 82 Überwachung rechtliche Bedenken.......................................... 697 Ubuntu........................................................................ 513 UE-V 씮 User Experience Virtualization Undo-Log ................................................................... 549 Unified Messaging Server ..........................535, 538 Unterbrechungsfreie Stromversorgung ....... 305 Unternehmenseigene Zertifizierungsstelle ........................................................................ 605 Unterstütztes Gast-Betriebssystem ................... 80 Update Fehler rückgängig machen ............................ 482 fehlerhaftes .......................................................... 654 Update Sequence Number .................................. 640 Rollback ................................................................. 640 Update-Ausführungsprofil ........................332, 333 Update-Basislinie.................................................... 617 Update-Katalog........................................................ 590 Uplink-Port-Profil................................................... 575 USB Anschluss lokaler Geräte ................................... 83 USB-auf-Ethernet-Adapter ............................. 393 USB-Festplatte in einer VM ............................ 423 USB-Platte für Server vermeiden ................. 230 USB-Schnittstelle in einer VM ....................... 392 User Experience Virtualization......................... 807 USN 씮 Update Sequence Number USN Rollback ......................................... 524, 525, 746 USV 씮 Unterbrechungsfreie Stromversorgung V V2V................................................................52, 554, 733 Vanderpool...................................................................63 VCO 씮 Virtual Computer Object vCPU................................................................................81 Prozessorfunktion einschränken ....................83 vCPU 씮 Virtuelle CPU VDA 씮 Lizenzierung VDev 씮 Virtual Device VDI 씮 Virtual Desktop Infrastructure VDI 씮 Virtuelle Desktop-Infrastruktur Veeam ONE für Hyper-V...................................... 706 Verbindungs-Broker.....................................761, 764 Verbrauchsmessung.............................................. 447 Verfügbarkeit ........................................................... 277 Definition .............................................................. 278 zugesagte .............................................................. 282 Verfügbarkeitsklasse ............................................. 281 Verkleinern VHD-/VHDX-Datei ............................................ 419 Versicherungspolice.............................................. 287 Vertrauensstellung ................................................ 675 Verwaiste Ressourcen ........................................... 590 Verwaltungsbetriebssystem .............................. 178 VF 씮 Virtual Function VFD 씮 Virtual Floppy Disk VHD 씮 Virtual Hard Disk VHD-Datei.................................................................. 588 VHDX 씮 Virtual Hard Disk Extended Viel hilft viel....................................................... 24, 390 VIP-Profil 씮 Virtual Machine Manager VIP-Vorlage 씮 Virtual Machine Manager Virenscanner ............................................78, 263, 266 Virtual-to-Virtual-Migration 씮 V2V Virtual Computer Object ..................................... 298 Virtual Desktop Infrastructure....... 107, 129, 418 Virtual Device..............................................................71 Virtual Floppy Disk ................................................ 466 Virtual Function...................................................... 436 Virtual Hard Disk Extended ............................... 494 Virtual Hard Disk ..........................................414, 494 erweitern ............................................................... 419 im Host einbinden ............................................. 467 komprimieren...................................................... 419 konvertieren......................................................... 419 verkleinern ............................................................ 419 Virtual IDE Controller ........................................... 705 Virtual Iron...................................................................46 843 Index Virtual LAN...................................... 78, 260, 347, 574 VLAN-ID ................................................................. 190 VLAN-ID, virtuelle Netzwerkkarte ............... 434 Virtual Machine Generation ID ........................ 524 Virtual Machine Health Summary .................. 704 Virtual Machine Management Service ............. 69 Virtual Machine Manager ......253, 254, 296, 333, 553, 597, 600, 673, 703 Administrator-Rolle .......................................... 717 Agent...........................................562, 590, 628, 740 Anwendungsadministrator ..................578, 579 Anwendungspaket ............................................ 582 Anwendungsprofil ....................................582, 583 Anwendungsskript ............................................ 582 Auftrag ................................................................... 582 Ausführungskonto ......................... 566, 569, 584 Benutzerrolle ........566, 578, 579, 600, 601, 607 Bibliothek ...............554, 562, 582, 588, 599, 624 Bibliotheksfreigabe ........................ 477, 578, 589 Bibliotheks-Server ..................555, 557, 571, 589 Cloud.....556, 566, 579, 584, 595, 596, 597, 608 Cloud-Bibliothek................................................. 588 Cloud-Kapazität ................................................. 596 Compliance-Management ............................. 554 Datenbank ............................................................ 738 Dienstkonto.......................................................... 739 Dienstvorlage .............................................582, 583 Dynamic Optimization.................................... 575 Fabric ..........................................573, 586, 624, 628 Fabric-Administrator ....................................... 578 Fabric-Management ...................... 554, 566, 570 File System ............................................................... 47 Funktionsprofil .......................583, 584, 586, 599 Gast-Betriebssystem-Profil 579, 583, 584, 600 Hardware-Profil............ 579, 583, 585, 586, 620 Host-Gruppe ............................566, 579, 610, 614 Host-Profil ......................................... 583, 587, 599 Konfigurationsanbieter................................... 580 Lastenausgleich.................................................. 610 Lastenausgleichsmethode.............................. 575 Lastenausgleichsmodul..........................574, 597 logischer Switch.................................................. 575 logisches Netzwerk......................... 574, 592, 597 MAC-Adress-Pool ............................................... 574 Management Pack ............................................ 714 Mandantenadministrator.............................. 578 Mandantenfähigkeit ........................................ 596 Migration .............................................................. 735 Netzwerkstandort.............................................. 574 Port-Gruppe ......................................................... 621 Port-Klassifizierung .................................575, 597 844 Port-Profil.............................................................. 576 Power Optimization.............555, 575, 610, 612, 614, 625 Self-Service Portal .............................................. 739 Self-Service-Benutzer ...............................578, 588 Self-Service-Benutzergruppe.......................... 606 Self-Service-Benutzerrolle ......................587, 600 SQL Server-Profil........................................583, 587 Storage-Management ...................................... 554 Verwaltungskonsole .............541, 564, 565, 712 Verwaltungs-Server........................................... 562 VIP-Profil ............................................................... 597 VIP-Vorlage .......................................................... 574 Virtual Center .........................................................47 virtuelle Anwendung ........................................ 582 VMM-Vorlage ...................................................... 566 VM-Vorlage .......................................................... 589 Vorlage................................................................... 259 Webanwendung.................................................. 582 Virtual Machine Monitor .......................................55 Virtual Machine Queue ..................... 183, 435, 576 Virtual Machine Servicing Tool ........................ 501 Virtual Machine Worker Process.........................70 Virtual PC ...............................................................46, 50 Virtual PC 씮 Microsoft Virtual Server 씮 Microsoft Virtual Storage Device .......................................... 705 VirtualBox ................................................................. 821 VirtualBox 씮 Oracle Virtual-Floppy-Format ......................................... 400 Virtualisierung Präsentation ........................................................ 757 warum? .....................................................................32 Virtualisierungs-Host ..................................762, 765 Virtualisierungs-Stack .............................................69 Virtualisierunsgprojekt Planung.....................................................................32 Virtualization Service Client .................................72 Virtualization Service Provider............................72 Virtualization Stack ..................................................69 VirtualManagerDB ................................................. 561 Virtual-Netzwerkadapter..................................... 705 Virtuelle CPU ............................................................ 406 Virtuelle Desktop-Infrastruktur .............107, 129, 418, 758 Virtuelle Festplatte................................................. 413 in einer VM ........................................................... 395 kopieren ................................................................. 637 zum Datenaustausch ....................................... 466 Virtuelle Floppy Disk zum Datenaustausch ....................................... 466 Index Virtuelle Hardware................................................. 396 dimensionieren ................................................... 390 Virtuelle Maschine................................................. 389 anhalten ................................................................ 462 Anzeigename....................................................... 401 Arbeitsspeicher ................................................... 402 COM-Port .............................................................. 400 Diskettenlaufwerk ............................................. 400 Export ............................................................488, 638 exportieren ........................................................... 488 Festplatte............................................................... 413 Fibre Channel....................................................... 429 IDE-Controller ..................................................... 398 im Cluster erzeugen .......................................... 349 Import..................................................................... 488 importieren .......................................................... 490 Integrationsdienst ....................................401, 462 kopieren ................................................................. 492 Netzwerkkarte..................................................... 430 neu starten ........................................................... 462 NIC-Teaming........................................................ 439 physische Festplatte.......................................... 420 Prozessor ............................................................... 405 Remote Desktop aktivieren............................ 468 Ressource .............................................................. 391 SAN-Datenträger................................................ 423 SCSI-Controller.................................................... 399 Snapshot................................................................ 462 USB-Festplatte..................................................... 423 zurücksetzen ........................................................ 462 Virtueller Datenträger Storage Space ...................................................... 231 Virtuelles Gerät .......................................................... 71 Virtuelles Netzwerk im Management OS einrichten .................... 191 Virtuelles SAN .......................................................... 429 VLAN 씮 Virtual LAN VM 씮 Virtuelle Maschine VM Vid Partition ..................................................... 705 VMBus............................................................................ 64 VMConnect ......................................................445, 459 VMDK 씮 VMware VMFS 씮 Virtual Machine Manager, File System VMFS 씮 VMware VM-Generation ID.........................................524, 527 vmickvpexchange .................................................. 441 VMM 씮 Virtual Machine Manager VM-Monitoring ....................................................... 707 VMMS 씮 Virtual Machine Management Service vMotion 씮 VMware VMQ 씮 Virtual Machine Queue VM-Replikation ..............................................354, 366 Authentifizierung............................ 368, 370, 376 Domänencontroller .......................................... 526 Erstkopie................................................................ 373 Failover-TCP/IP ................................................... 375 geplantes Failover ............................................. 384 Hyper-V Replica Log ......................................... 367 Kompression ...............................................370, 376 Replikat .........................................................366, 379 Replikat-Server........................367, 370, 372, 387 Synchronisation ................................................. 378 Testfailover........................................................... 381 Testreplikat........................................................... 382 Wiederherstellungspunkt ........... 367, 372, 376, 381, 387 VM-Replikation 씮 Hyper-V Replica VM-Snapshot für SQL Server ...................................................... 545 VMST 씮 Virtual Machine Servicing Tool VM-Vorlage ...............265, 472, 473, 474, 476, 477, 589, 608 VMware....................................................................... 572 ESX .....................47, 554, 584, 597, 610, 621, 737 ESX 3.5..................................................................... 622 ESX 4.1 ..................................................................... 622 ESX Server .........................................................57, 63 ESX Server 2.5 ..........................................................46 ESXi................................................................... 47, 621 ESXi 3.5.................................................................... 622 ESXi 4.1.................................................................... 622 GSX Server.........................................................46, 58 Player ...................................................................... 821 Server ..................................................................46, 58 Tools ........................................................................ 734 vCenter ......................................... 48, 571, 621, 623 vCenter 4.1 ............................................................. 622 vCenter 5.1 ............................................................. 622 vCenter Server ..................................................... 737 VMDK............................................................... 48, 621 vMotion ................................................... 48, 63, 621 vSphere.................................. 19, 47, 553, 554, 573 vSphere Hypervisor ..............................................57 vSphere Server 5.1 ..................................................47 Workstation ......................................................... 821 VMWP 씮 Virtual Machine Worker Process Vollredundanz ......................................................... 285 Volume im Storage Space................................................ 234 845 Index Volume Shadow Copy Service....... 297, 442, 542, 636, 638, 646, 672, 683 Hardware-Provider ........................................... 683 Software-Provider.............................................. 683 Voter 씮 Failover-Cluster VSC 씮 Virtualization Service Client VSP 씮 Virtualization Service Provider vSphere 씮 VMware VSS 씮 Volume Shadow Copy Service vSwitch Name im Cluster................................................. 347 W Wachstum unkontrolliertes..................................................... 36 Wahrsam, Inge............................................................ 43 WAN 씮 Wide Area Network Warnung Best Practices Analyzer....................................... 74 Warteschlange für virtuelle Computer.......... 435 Wartungsfenster ..................................................... 580 Wartungsmodus ..................................................... 611 Wartungsplan........................................................... 692 Wartungsvorgang Ausfallzeit ............................................................. 282 Wasserschaden ........................................................ 650 Wasserzähler ............................................................ 449 WDS 씮 Windows Deployment Services WebAccess .............................................. 762, 763, 784 Webserver für SharePoint ..................................................... 551 Webserver-Zertifikat ............................................. 605 Weight Bandbreiten-Reservierungsmodus ............. 192 Werkzeug Datenwiederherstellung ................................. 631 WFP 씮 Windows Filtering Platform WID 씮 Windows Internal Database Wide Area Network ................................................ 675 Wiederanlaufzeit entworfene............................................................ 818 Wiederherstellen VM über Snapshot ............................................. 478 Wiederherstellung ................................................. 710 Host-Server........................................................... 651 planen..................................................................... 649 Qualität.................................................................. 633 Wiederherstellungszeit........................................ 647 WIM 씮 Windows Imaging Format 846 Windows 8 ........................................................100, 680 App Bar................................................................... 796 Charms ..........................................................785, 796 Einschränkung bei der Hyper-VNutzung ............................................................ 101 Hyper-V-GUI-Verwaltungstools................... 103 Windows 8 Server ......................................................20 Windows Assessment and Deployment Kit .........................................509, 558 Windows Automated Installation Kit ............ 736 Windows Azure...............................................602, 673 Windows Deployment Services ..... 430, 557, 572 Windows Filtering Platform...178, 179, 181, 575 Windows Imaging Format .................................. 494 Windows Internal Database ............................... 765 Windows Management Instrumentation .... 331 Windows Network Load Balancing.................. 764 Windows NT 4.0 Prozessorkompatibilität ................................. 411 Windows Remote Management ..............331, 558 2.0............................................................................. 736 Windows Server 2003 ........................................... 680 Windows Server 2008 R2..................................... 680 Windows Server 2012 Editionen und Lizenzen ................................... 810 Essentials............................................................... 810 Foundation ........................................................... 810 Windows Server Backup 씮 Windows Server-Sicherung Windows Server Failover-Cluster..................... 290 Windows Server Update Services...........331, 500, 501, 557, 571, 615, 616 Windows Server-Sicherung .......................656, 691 Archivattribut...................................................... 660 Einmalsicherung ................................................ 659 NTBACKUP............................................................ 656 Sicherungszeitplan ............................................ 659 Wiederherstellung.............................................. 667 Windows System Image Manager ................... 509 Windows Update..................................................... 494 auf Host-Servern ................................................ 444 Windows Update-Katalog.................................... 573 Windows XP .............................................................. 680 Windows-Failover-Cluster 씮 Failover-Cluster Windows-Failover-Cluster-Umgebung .......... 688 Windows-Firewall ..... 266, 312, 358, 369, 468, 585 WinRM 씮 Windows Remote Management Wissensdatenbank ................................................. 706 WMI 씮 Windows Management Instrumentation Wolfpack..................................................................... 292 Index World Wide Name .........................................219, 429 World Wide Node Name ...................................... 219 World Wide Port Name ........................................ 219 Worldwide Name ....................................................... 82 WSFC 씮 Windows Server Failover-Cluster WSMan........................................................................... 98 WSUS 씮 Windows Server Update Services WWN............................................................................... 82 WWN 씮 World Wide Name WWNN 씮 World Wide Node Name WWPN 씮 World Wide Port Name www.gruppenrichtlinien.de ............................... 529 X XenApp 씮 Citrix XenServer 씮 Citrix XP Mode ........................................................................ 59 Z Zähler für VM-Ressourcen ............................................ 457 Zeitplaner................................................................... 117 Zeitpunkt VM wiederherstellen......................................... 477 Zeitscheibenprinzip........................................ 55, 389 Zeit-Server ................................................................. 527 Zeitsynchronisation im Active Directory ........................................... 527 Integrationsdienst ............................................. 440 Zertifikat..................................................................... 623 selbst signiert....................................................... 605 Subject Alternate Name .................................. 606 Webserver.............................................................. 605 Zeugendatenträger ............................. 307, 310, 316 Zeugenfreigabe........................................................ 308 Ziel definieren .................................................................35 der Virtualisierung ...............................................33 des Unternehmens................................................34 Zielgruppe.................................................................. 804 Knowledge Worker ............................................ 759 Power User............................................................ 760 Systemadministration ..................................... 760 Task Worker ......................................................... 759 Zurücksetzen VM............................................................................ 462 Zusammenführen von Snapshots ..................................................... 486 Zustand einer VM wiederherstellen ................................................. 477 Zwei-Knoten-Cluster ............................................. 726 Zwischenablage ....................................................... 464 Inhalt an eine VM senden............................... 463 847