Inhalt - Thorsten Jarz
Werbung

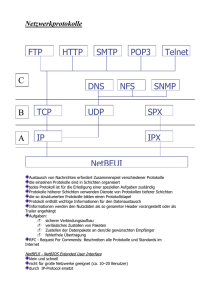
Netzwerktechnik Seite 1 Inhalt 1. 2. 2.1 2.2 2.3 2.4 2.5 2.6 2.7 2.8 2.9 2.10 3. 3.1 3.2 3.3 3.4 3.5 3.6 4. 4.1 4.2 4.3 4.4 4.5 4.6 5. 5.1 5.2 6. 6.1 6.2 6.3 6.4 6.5 6.6 6.7 6.8 6.9 6.10 6.11 7. 7.1 7.2 7.3 7.4 7.5 7.6 7.7 Topologien ................................................................................................................................. 3 Kabelgebundene Datenübertragung....................................................................................... 5 Dienste ................................................................................................................................... 5 Übertragungsarten und Geschwindigkeiten ........................................................................... 5 Strukturierte Verkabelung im LAN (Ethernet) ...................................................................... 7 Datenübertragungsraten, Frequenzen und Codierung ............................................................ 8 Verschiedene Leistungsqualitäten.......................................................................................... 9 Twisted Pair Verkabelung.................................................................................................... 10 Beispiel einer Verkabelung .................................................................................................. 14 Lichtwellenleiter (=Glasfaserkabel) ..................................................................................... 16 Kabelgebundenes Ethernet (802.3) ...................................................................................... 18 Wiederholungsfragen ........................................................................................................... 20 Drahtlose Übertragung .......................................................................................................... 21 Das elektromagnetische Spektrum, Frequenzbereiche ........................................................ 21 WLAN (802.11, WiFi) ......................................................................................................... 23 Absicherung eines WLANs ................................................................................................. 25 Bluetooth (802.15) ............................................................................................................... 26 Datenübertragung in Mobilfunknetzten ............................................................................... 27 Wiederholungsfragen ........................................................................................................... 27 Medienzugriffsverfahren ....................................................................................................... 29 ALOHA ............................................................................................................................... 29 CSMA/CD ........................................................................................................................... 29 Token Passing ...................................................................................................................... 30 Demand Priority ................................................................................................................... 31 CSMA/CA ........................................................................................................................... 31 Wiederholungsfragen ........................................................................................................... 31 Das OSI – Referenzmodell ..................................................................................................... 33 Die Schichten ....................................................................................................................... 33 Wiederholungsfragen ........................................................................................................... 36 Das TCP/IP Protokoll ............................................................................................................ 37 Protokolle ............................................................................................................................. 37 TCP/IP Grundlagen .............................................................................................................. 37 IPv4-Adressierung ............................................................................................................... 38 Portnummer - Sockets .......................................................................................................... 41 Domain Name Service (DNS).............................................................................................. 42 DHCP (Dynamic Host Configuration Protocol) .................................................................. 44 IP Multicast .......................................................................................................................... 46 NAT ..................................................................................................................................... 46 Ein Beispiel zu TCP/IP ........................................................................................................ 47 IPv6 ...................................................................................................................................... 48 Wiederholungsfragen ........................................................................................................... 50 Wichtige TCP/IP Protokolle .................................................................................................. 51 Address Resolution Protocol (ARP) .................................................................................... 51 Internet Control Messaging Protocol (ICMP) ...................................................................... 52 Internet Protocol (IPv4) ....................................................................................................... 53 Transmission Control Protocol (TCP) ................................................................................. 54 User Datagram Protocol (UDP) ........................................................................................... 55 Hypertext Transfer Protocol (HTTP) ................................................................................... 56 Simple Mail Transfer Protocol (SMTP) / Extended SMTP (ESMTP)................................. 58 ©Thorsten Jarz Seite 2 7.8 7.9 7.10 7.11 8. 8.1 8.2 8.3 8.4 8.5 8.6 8.7 9. 9.1 10. V 6.0 Netzwerktechnik Post Office Protocol Version 3 (POP3) ............................................................................... 58 Standardisierung mit Hilfe von RFCs .................................................................................. 59 Wichtige Netzwerkbefehle in Microsoft Windows und Linux ............................................ 59 Wiederholungsfragen ........................................................................................................... 63 Aktive Komponenten ............................................................................................................. 65 Repeater ............................................................................................................................... 65 Hub....................................................................................................................................... 65 Bridge ................................................................................................................................... 66 Switch .................................................................................................................................. 67 Router ................................................................................................................................... 69 Gateway ............................................................................................................................... 71 Wiederholungsfragen ........................................................................................................... 71 Firewall .................................................................................................................................... 73 Wiederholungsfragen ........................................................................................................... 75 Stichwortverzeichnis .............................................................................................................. 77